Zero Trust Network Architecture vs Zero Trust: What Is the Difference?
Joseph Steinberg
JANUARY 4, 2023
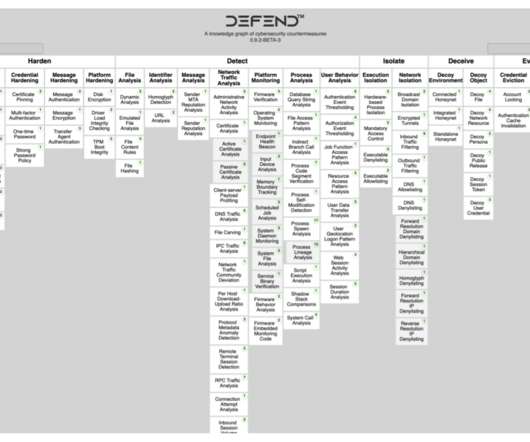
Zero Trust is a term that is often misunderstood and misused, which is why I wrote an article not long ago entitled Zero Trust: What These Overused Cybersecurity Buzz Words Actually Mean – And Do Not Mean. Zero Trust Network Architecture is an architecture of systems, data, and workflow that implements a Zero Trust model.

















































Let's personalize your content