Top 7 Cloud Storage Security Issues & Risks (+ Mitigations)
eSecurity Planet
JANUARY 30, 2024
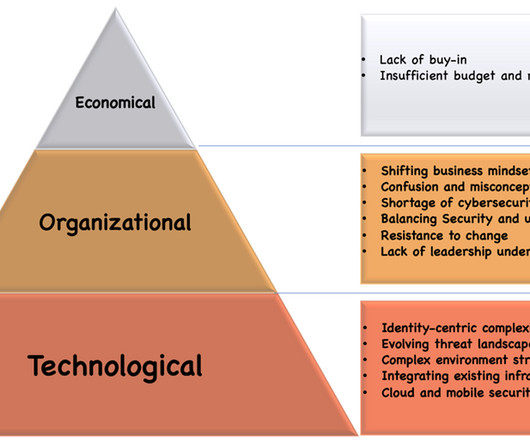
Cloud storage risks involve potential external threats and vulnerabilities that jeopardize the security of stored data. Risks can lead to issues, but at the same time, you can prevent the risks by addressing these issues. Migration challenges result in incomplete transfers, which expose critical information to risk.















































Let's personalize your content