Passwordless Protection: The Next Step in Zero Trust
Cisco Security
AUGUST 4, 2021
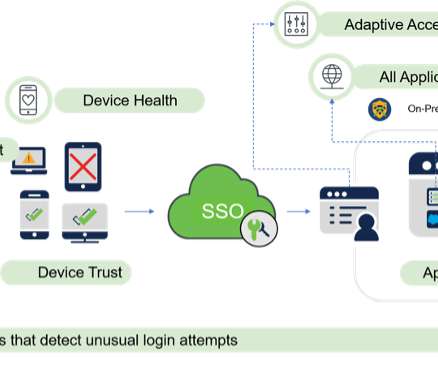
Deploying a Zero Trust architecture for the workforce provides a series of benefits, including improving the end-user experience by allowing access to some applications or resources that traditionally require VPN access and streamlining authentication through multi-factor authentication (MFA). The Move to Passwordless.































Let's personalize your content