Passwordless Protection: The Next Step in Zero Trust
Cisco Security
AUGUST 4, 2021
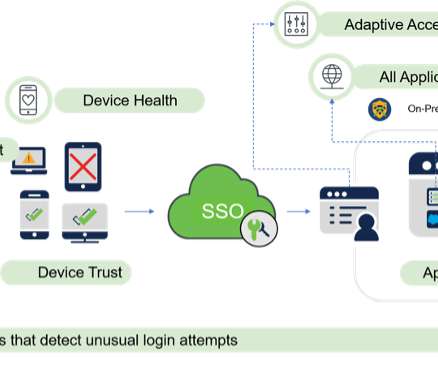
Zero Trust principles help protect against identity and access-based security risks by requiring all users, whether inside or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture checks before granted access to applications and data.





























Let's personalize your content