SHARED INTEL Q&A: My thoughts and opinions about cyber threats — as discussed with OneRep
The Last Watchdog
OCTOBER 5, 2023
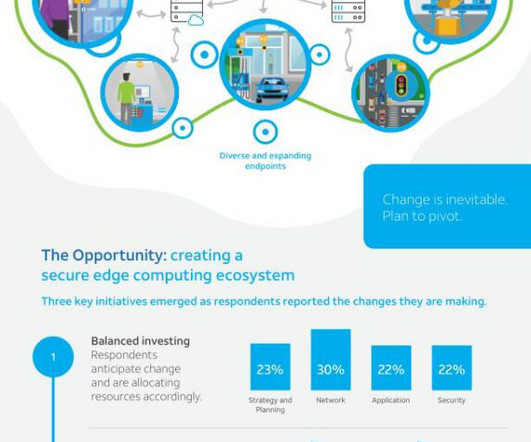
A shift from legacy, perimeter-focused network defenses to dynamic, interoperable defenses at the cloud edge, directed at ephemeral software connections, must fully play out. These emergent software and hardware advances will pave the way for factoring in quantum computers.




























Let's personalize your content