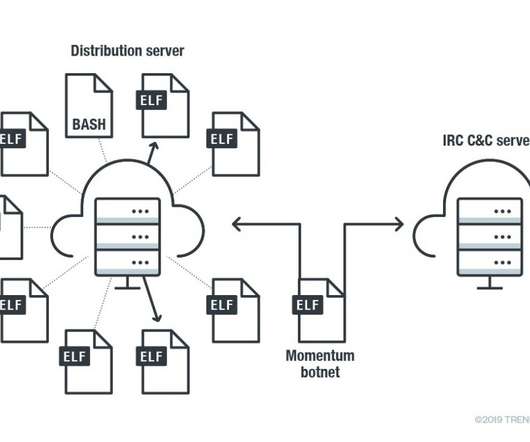
Trend Micro observed notable malware activity associated with the Momentum Botnet
Security Affairs
DECEMBER 18, 2019
The Momentum bot targets various Linux platforms running upon multiple CPU architectures, including ARM, MIPS, Intel, and Motorola 68020. ” Momentum supports 36 different methods for DDoS attacks, including multiple reflection and amplifications attack methods that target MEMCACHE , LDAP , DNS and Valve Source Engine.
















Let's personalize your content