Looking at a penetration test through the eyes of a target
CyberSecurity Insiders
MAY 3, 2023
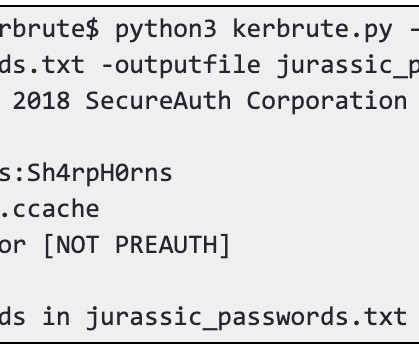
AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Penetration testing (pentesting) is one of the fundamental mechanisms in this area. The content of this post is solely the responsibility of the author.



























Let's personalize your content