Beyond Perimeter Defense: Making Attack Surface Management a Business Enabler
Tech Republic Security
JUNE 1, 2025
As cyber threats outpace traditional perimeter defenses, organizations face mounting risks in their digital transformation efforts.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JUNE 1, 2025
As cyber threats outpace traditional perimeter defenses, organizations face mounting risks in their digital transformation efforts.

CSO Magazine
APRIL 21, 2023
While indicators of compromise (IoCs) and attackers’ tactics, techniques, and processes (TTPs) remain central to threat intelligence, cyber threat intelligence (CTI) needs have grown over the past few years, driven by things like digital transformation, cloud computing, SaaS propagation, and remote worker support.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
AUGUST 29, 2023
Here’s what you should know about the risks, what aviation is doing to address those risks, and how to overcome them. It is difficult to deny that cyberthreats are a risk to planes. Risks delineated Still, there have been many other incidents since. Fortunately, there are ways to address the risks.

Joseph Steinberg
JANUARY 12, 2021
Without threat intelligence, cybersecurity pros often choose to address the vulnerabilities that *only in theory* pose the greatest risks if exploited – an approach which often leads to severe problems. In a future piece I will explore the various types of threat intelligence – stay tuned. Click To Tweet.

SecureWorld News
DECEMBER 9, 2024
Tasked with safeguarding data and infrastructure, CISOs face mounting pressures as cyber threats escalate, regulatory demands grow, and the role expands to encompass strategic business responsibilities. Stress and burnout are leading contributors, with 60% citing stress and 53% citing burnout as risks that could prompt them to leave.
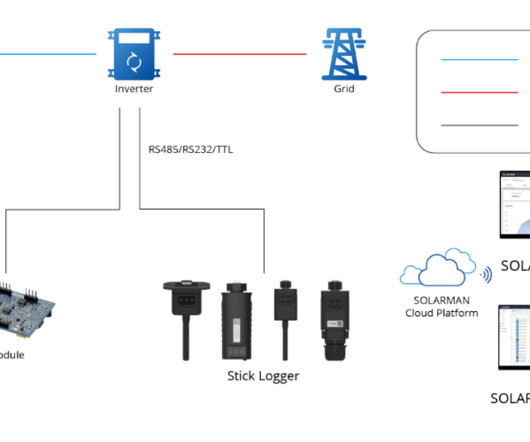
Security Affairs
FEBRUARY 28, 2025
Hackers reveal security flaws in smart solar systems, exposing risks to national power grids as global reliance on solar energy grows. DW investigated the risks of cyber attacks exploiting vulnerabilities in smart solar systems while the demand for solar energy grows. ” reads the article published by DW.

CSO Magazine
FEBRUARY 28, 2023
Companies rightly see much promise for future revenues and productivity by building and participating in emerging digital ecosystems — but most have not given enough consideration to the risks and threats inherent in such ecosystems.

SecureWorld News
FEBRUARY 4, 2025
officials began seriously discussing the creation of a military Cyber Force dedicated to thwarting cyberattacks. However, the answer to cyber threats is proactivity. Although some of the risks of localization for cybersecurity are unpredictable emergent occurrences, most of them can be tackled preemptively. EU, and China.

SecureWorld News
APRIL 13, 2025
Cyber threats evolve daily, often outpacing traditional security measures. On defense, AI analyzes network traffic, detects anomalies, and responds to threats in real time. Unlike traditional signature-based systems, AI excels at identifying new and unknown cyber threats, making security stronger and more adaptive.

Trend Micro
JANUARY 10, 2024
Trend Micro collaborates with INTERPOL to defend FIFA World Cup by preventing attacks & mitigating risks to fight against the rising threat of cybercrime.

Security Boulevard
JANUARY 10, 2022
We published a whitepaper about Tactics, Techniques, and Procedures (TTPs) and also tools utilized by the DarkSide threat actors. . Practice risk management for the worst case event. When ransomware threat actors infect a critical infrastructure, they hold hostage both the company and its customers. Lessons Learned: 3.

Security Boulevard
MARCH 6, 2025
By Oleg Lypko, with Estelle Ruellan and Tammy Harper (Flare Research) This article has originally appeared on Cybercrime Diaries On February 20, 2025, the cybersecurity community received an unexpected stroke of luck as internal strife seemingly spread within the infamous Black Basta ransomware group.

CSO Magazine
MAY 25, 2023
Survey respondents were asked questions about their organization’s cyber-threat intelligence (CTI) program – how it was staffed, what types of skills were most important, its challenges and strategies, spending plans, etc. The first one gave an overview of enterprise threat intelligence programs. more than 1,000 employees).

CSO Magazine
JANUARY 24, 2023
Industry respondents also expressed concerns over identity theft at 4%, unavailable or unaffordable cyber insurance at 4%, geopolitical risks at 3%, DDoS attacks at 2% and website defacement at 0.9%, according to CSI’s annual survey of the financial sector. To read this article in full, please click here

eSecurity Planet
FEBRUARY 17, 2023
Threat hunting starts with a pretty paranoid premise: That your network may have already been breached and threat actors may be inside waiting for an opportunity to strike. This data is based on common attributes where cyber threat hunters can efficiently identify suspicious activity, making the threat hunting process more manageable.

CSO Magazine
MARCH 9, 2022
When reviewing your network for potential cyber threats, don’t make things worse by making misconfigurations that will create more problems. To read this article in full, please click here Take care of security basics first. Spend time on the basics and on other projects that you probably should have worked on earlier.

Hacker's King
OCTOBER 26, 2024
Activities during this week include engaging workshops, informative webinars, and community events, all designed to empower individuals with the knowledge and skills necessary to navigate today’s cyber threats effectively. Stay Informed: Cyber threats are constantly evolving.

Trend Micro
NOVEMBER 15, 2021
To succeed in the post-pandemic era, organizations must come to a shared understanding about cybersecurity as a critical element of business risk. The digital transformations that accompanied the pandemic are here to stay.

Identity IQ
MAY 15, 2023
Juice Jacking: The Latest Cyber Threat to Your Personal Information and Devices IdentityIQ Juice jacking, a new cybercrime trend, is targeting people who charge their phones or tablets at public charging stations. Bottom Line Juice jacking can put your personal information and smart devices at risk.

Schneier on Security
JULY 24, 2019
But, in the world of cybersecurity, we do not deal in absolute guarantees but in relative risks. All systems fall short of optimality and have some residual risk of vulnerability a point which the tech community acknowledges when they propose that law enforcement can satisfy its requirements by exploiting vulnerabilities in their products.

The Last Watchdog
JANUARY 29, 2020
An effective cyber strategy is normally on par with the cybersecurity risk exposure of an entity. Editor’s note : This is an excerpt from Cybersecurity – Attack and Defense Strategies, Second Edition , a detailed overview of Cloud Security Posture Management ( CSPM ) and an assessment of the current threat landscape.

Security Boulevard
JANUARY 1, 2024
The United States Cybersecurity and Infrastructure Security Agency (CISA) recently conducted a Risk and Vulnerability Assessment (RVA), delving into the cybersecurity posture of an unnamed HPH organization utilizing on-prem software.

Security Boulevard
MARCH 31, 2025
Articles related to cyber risk quantification, cyber risk management, and cyber resilience. The post CRQ & CTEM: Prioritizing Cyber Threats Effectively | Kovrr appeared first on Security Boulevard.

The Last Watchdog
DECEMBER 5, 2019
I’m privileged to share news that two Last Watchdog articles were recognized in the 2019 Information Management Today MVP Awards. Cyber threats to privacy and security will continue to be a seminal issue that affects us all for the foreseeable future. I’ve never done stories to win awards.

Trend Micro
JANUARY 7, 2022
The first of a series of blog posts examines the security risks of Codex, a code generator powered by the GPT-3 engine.

Trend Micro
OCTOBER 11, 2021
Read this article to learn more. Security leaders are seeking new ways to minimize SecOps security monitoring tools while increasing efficiency for SecOps teams.

The Last Watchdog
FEBRUARY 20, 2024
Machine learning helps AI chatbots adapt to and prevent new cyber threats. While AI chatbots have cybersecurity vulnerabilities, adopting proactive measures like secure development practices and regular assessments can effectively mitigate risks.

SecureWorld News
JANUARY 10, 2025
In this article, we'll look at seven ways retail businesses can benefit from the power of retail analytics tools without compromising their cybersecurity measures. When we talk about secure payment analytics, we are looking at technology that can monitor transactions in real-time and reduce the risk of payment fraud.

SecureWorld News
JANUARY 12, 2025
A 2022 PwC study found that 59% of directors admitted their board is not very effective in understanding the drivers and impacts of cyber risks for their organization, emphasizing the critical role of board members in these moments. Only a select group of properly trained individuals should escalate cyber incidents to the board.

Hacker's King
OCTOBER 20, 2024
While cybersecurity primarily aims to protect users from threats like malware, hacking, and data breaches, some tools can monitor or track user activities in certain situations. This article will explore whether cybersecurity involves tracking and under what circumstances it might happen. What Is Cybersecurity?

CSO Magazine
JUNE 16, 2021
Firewalls, anti-virus, endpoint protection, and security awareness all form a foundation of protection against cyber threats. Today, organizations need tools that allow them to ask detailed questions to identify advanced (and even invisible) threats and active adversaries, and quickly take appropriate action to stop them.

SecureWorld News
MAY 2, 2025
The healthcare sector faces an unprecedented wave of cyber threats, which in turn is fueling record growth in cybersecurity spending. Breaches can disrupt care delivery and put lives at risk, not to mention lead to hefty compliance fines. The market's expected ris e to $82.9

CSO Magazine
JULY 14, 2022
There are such varied and rapidly changing facets of defending organizations against cyber threats that the task of sorting out which risks need the most attention can seem overwhelming. To read this article in full, please click here

CyberSecurity Insiders
JUNE 6, 2023
AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Numerous risks are inherent in the technologies that all organizations use. This discussion will focus on how GRC, or governance, risk, and compliance can help organizations face and manage the risks that they face.

Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.

Joseph Steinberg
FEBRUARY 9, 2021
If you have not yet read my article on the aforementioned subject, I strongly suggest taking a look.). CrowdSec, however, does not base its analysis of traffic solely on earlier traffic received by the local site – it leverages the entire community of CrowdSec users to study traffic and determine what seems to pose the greatest risks.

Trend Micro
FEBRUARY 23, 2022
As global tension rises, cyber-risk management and security fundamentals are the key to cyber-resilience. 5 best practices are presented to manage your cyber risk.

Hacker's King
DECEMBER 21, 2024
The proliferation of cyber threats demands innovative solutions, and generative AI is emerging as a transformative force in this arena. Far beyond its applications in content creation or virtual assistants, generative AI is revolutionizing cybersecurity by enhancing threat detection, automating responses, and fortifying defenses.

Trend Micro
JUNE 19, 2023
In this entry, we document the techniques used to spread and abuse SeroXen, as well as the security risks, impact, implications of, and insights into highly evasive FUD batch obfuscators. This is the third installment of a three-part technical analysis of the fully undetectable (FUD) obfuscation engine BatCloak and SeroXen malware.

Hacker's King
MAY 24, 2025
In the contemporary and advanced society, cyber threats are on the rise in both quantity and sophistication. No day goes by without risk of data breaches, identity theft, or financial losses to both people and businesses around the world.

Hacker's King
DECEMBER 17, 2024
This article explores the workings of the new Linux FASTCash variant, its implications for the financial sector, and how organizations can mitigate its risks. YOU MAY ALSO WANT TO READ ABOUT: Recent Cyber Attacks: Trends, Tactics, and Countermeasures What is FASTCash?

CSO Magazine
APRIL 24, 2023
Threat intelligence firm Flashpoint has announced the release of Ignite, a new intelligence platform built to accelerate cross-functional risk mitigation and prevention across vulnerability management and security teams, including those in law enforcement, state and local government, and federal civilian agencies.

Security Affairs
MARCH 8, 2025
Every week the best security articles from Security Affairs are free in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

eSecurity Planet
SEPTEMBER 21, 2024
Understanding and adhering to cybersecurity regulations is crucial for any organization as cyber threats evolve and become more sophisticated. Let’s explore what to expect from the upcoming regulations, provide insights into critical federal and state laws, and offer practical compliance and risk management strategies.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content