Microsoft Signing Key Stolen by Chinese
Schneier on Security
AUGUST 7, 2023
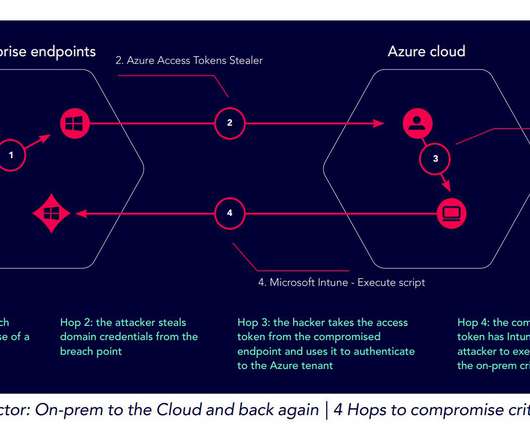
The hackers used forged authentication tokens to access user email, using a stolen Microsoft Azure account consumer signing key. The fact that Microsoft has not been forthcoming about the details of what happened tell me that the details are really bad. I believe this all traces back to SolarWinds.












Let's personalize your content