Digital Risk Types Demystified: A Strategic Insight into Online Threats
Centraleyes
APRIL 23, 2024
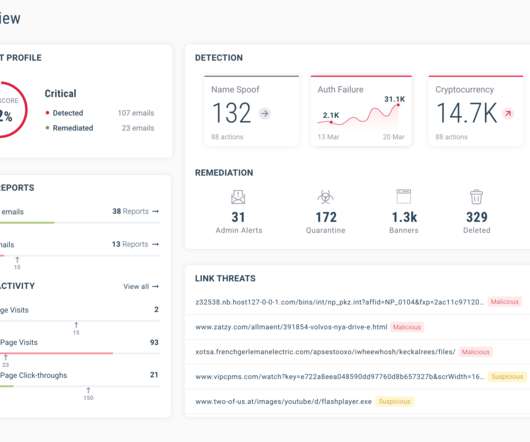
The digital landscape is advancing, and the risks of shirking cutting-edge technology are substantial. It’s well known that while new technologies open up novel pathways, they also come with risks. According to a recent Deloitte report , more than half (52%) of consumers feel more at risk in the digital environment.
































Let's personalize your content