Artificial intelligence (AI) as an Enabler for Enhanced Data Security
Security Affairs
FEBRUARY 11, 2025
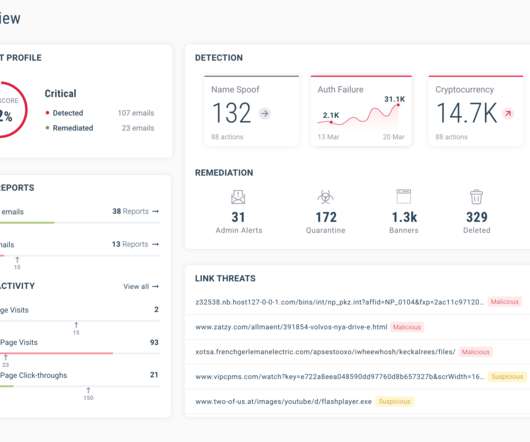
Artificial intelligence enhances data security by identifying risks and protecting sensitive cloud data, helping organizations stay ahead of evolving threats. Artificial intelligence (AI) is transforming industries and redefining how organizations protect their data in todays fast-paced digital world.

















































Let's personalize your content