Data Security Trends: 2024 Report Analysis
Thales Cloud Protection & Licensing
MARCH 24, 2024
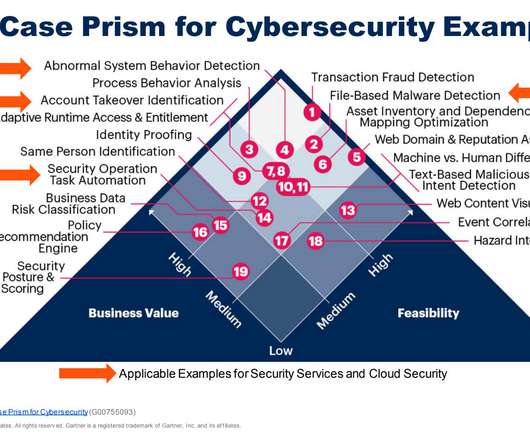
The report explores their experiences, hurdles, approaches, and achievements and offers insights into the security implications of new technologies and the organizational adaptations necessary for future success. This highlights a significant link between compliance adherence and data security.






























Let's personalize your content