Attack Surface Management vs. Vulnerability Management
The Hacker News
APRIL 3, 2024
Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 attack-surface-management
attack-surface-management 
The Hacker News
APRIL 3, 2024
Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same.

Security Boulevard
MARCH 21, 2024
Ordr this week added an attack surface management (ASM) tool infused with artificial intelligence (AI) to its existing asset management portfolio. The post Ordr Taps AI to Augment Attack Surface Management appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
MAY 31, 2023
The post Attack Surface Management Vs. Vulnerability Management appeared first on Security Boulevard. So many, in fact, that I would be hard-pressed to find someone who knows what they all stand for or clearly explain the subtle differences between many of them.

NetSpi Executives
JANUARY 30, 2024
As your company’s external attack surface expands and threat actors remain relentless, Attack Surface Management (ASM) solutions can help level up your proactive security measures by enabling continuous pentesting.

eSecurity Planet
DECEMBER 20, 2023
Attack surface management (ASM) is a relatively new cybersecurity technology that combines elements of vulnerability management and asset discovery with the automation capabilities of breach and attack simulation (BAS) and applies them to an organization’s entire IT environment, from networks to the cloud.

NetSpi Executives
MARCH 19, 2024
Attack surface sprawl is a growing challenge with 76% of organizations experiencing some type of cyberattack that started through the exploit of an unknown, unmanaged, or poorly managed internet-facing asset. How NetSPI Attack Surface Management covers gaps The beauty of ASM is its ability to uncover what’s unknown.

Security Boulevard
DECEMBER 15, 2022
Following its acquisition of Reposify earlier this year, CrowdStrike today added external attack surface management (EASM) technology to the CrowdStrike Falcon platform. The post CrowdStrike Adds Attack Surface Management Module appeared first on Security Boulevard. At the same.

The Last Watchdog
JULY 27, 2022
Post Covid 19, attack surface management has become the focal point of defending company networks. A new category of attack surface management tools and services is gaining traction and fast becoming a must-have capability.

Security Boulevard
MAY 31, 2023
External attack surface management (EASM) has become a vital strategy for improving cybersecurity, particularly amid recession fears that have stressed the business landscape across several sectors for many months. This uptick highlighted.

Security Boulevard
APRIL 8, 2024
Here’s how you can protect your company’s data through a robust attack surface management strategy. The post What is Attack Surface Management (ASM) and How Has it Changed? The threat landscape to a business changes every day. appeared first on Security Boulevard.

The Last Watchdog
AUGUST 22, 2022
In short, attack surface management has become the main tent pole of cybersecurity. And now advanced weaponry is arriving that leverages data analytics to tighten up systems and smother attacks. This is why it makes so much sense for artificial intelligence, generally, to be brought to bear in attack surface management.

CSO Magazine
MARCH 21, 2023
Cyber asset attack surface management (CAASM) or external attack surface management (EASM) solutions are designed to quantify the attack surface and minimize and harden it.

The Hacker News
JULY 19, 2023
Attack surfaces are growing faster than security teams can keep up. To stay ahead, you need to know what's exposed and where attackers are most likely to strike.

Security Boulevard
JULY 13, 2023
Attack Surface Management (ASM) - what you need to know about its strengths and weaknesses when it comes to cyber resilience. The post Attack Surface Management (ASM) – What You Need to Know appeared first on SafeBreach.

NetSpi Executives
MARCH 5, 2024
Table of Contents What is External Attack Surface Management? The technology creates a comprehensive view of a company’s external assets by mapping the internet-facing attack surface to provide better insight into changes and where to focus the attention of security teams.

Heimadal Security
NOVEMBER 4, 2022
Attack surface management is an important practice many businesses should employ to secure their machines and systems. To defeat them, you must think like them, so attack surface management does exactly this. It allows you to approach security from the perspective of an attacker.

NetSpi Executives
JANUARY 30, 2024
As your company’s external attack surface expands and threat actors remain relentless, Attack Surface Management (ASM) solutions can help level up your proactive security measures by enabling continuous pentesting.

InfoWorld on Security
MAY 16, 2023
When it comes to securing cloud computing environments, one key aspect often goes overlooked: attack surface management (ASM). Attackers are getting better at what they do and now can weaponize artificial intelligence technology against you.

Security Boulevard
DECEMBER 13, 2023
Traditional asset inventory and vulnerability management software can’t keep up to date with the growing attack surface and morphing vulnerabilities. Contrary to other cybersecurity software, Attack Surface Management software operates. The post Attack Surface Management: What is it?
Security Boulevard
MARCH 6, 2024
The cloud revolutionized how businesses operate, but with increased flexibility comes an expanded attack surface. The post Cloud Attack Surface Management(CASM): What is it? The post Cloud Attack Surface Management(CASM): What is it? How does Strobes CASM help you with cloud security?

The Hacker News
MAY 11, 2023
According to Forrester, External Attack Surface Management (EASM) emerged as a market category in 2021 and gained popularity in 2022. Recognition from global analysts has officially put

CyberSecurity Insiders
SEPTEMBER 20, 2022
Earlier this year, I had the opportunity to speak before a group of CISOs about the topic of attack surface management (ASM). While much of the conversation centered around managing the attack surface around on-premise environments and cloud infrastructure, it was interesting to me that not much was said about SaaS.

The Hacker News
JUNE 12, 2023
The term "attack surface management" (ASM) went from unknown to ubiquitous in the cybersecurity space over the past few years. Many concepts come and go in cybersecurity, but attack surface management Many concepts come and go in cybersecurity, but attack surface management

CyberSecurity Insiders
JUNE 18, 2022
The attack surface of organizations is nowadays more complex than ever. As more and more businesses increase the number of their digital assets and incorporate new technology to operate, they turn their attack surface into an intricate network. Following Three Phases of the Attack Surface Management.

Security Boulevard
SEPTEMBER 29, 2022
The Attack Surface Has Grown with API Usage Application programming interfaces (APIs) help ensure a smooth running and engaging experience for mobile and web applications. The post External Attack Surface Management for APIs appeared first on Cequence Security. In addition, online business […].

Security Boulevard
JANUARY 4, 2024
This blog offers practical tips to assess the efficacy of an organization’s attack surface management strategy and how leaders can enhance it. The post Your Guide to Building a Successful Attack Surface Management Strategy appeared first on Security Boulevard.

CyberSecurity Insiders
OCTOBER 9, 2022
The external attack surface of companies continues to grow, presenting threat actors with a larger opportunity to gain access to exposed assets. In many cases, hackers find it easier to attack these assets and use them as entry points into a company’s technology system than a direct attack.

Trend Micro
JUNE 14, 2023
As organizations shift to the cloud in droves, their digital attack surface continues to rapidly expand. We explore how proactive cyber risk management can help harden your defenses and reduce the likelihood of an attack or breach.

Security Boulevard
FEBRUARY 7, 2023
The post Managing Your Attack Surface appeared first on Digital Defense. The post Managing Your Attack Surface appeared first on Security Boulevard.

CSO Magazine
JUNE 22, 2021
More cloud computing solutions, remote and work-from-home systems and internet-connected devices increase risk from an expanded attack surface. The best way to reduce the number of vulnerabilities is to establish a proper enterprise attack surface management program. Learn the 7 keys to better risk assessment. |

CSO Magazine
APRIL 24, 2023
Open source, cloud security firm Paladin Cloud has launched a new SaaS-based platform for enterprise cloud attack surface discovery and vulnerability management.

CSO Magazine
FEBRUARY 11, 2022
Attack surface management (ASM) is a somewhat confusing topic that starts with a fundamental question: What exactly is the attack surface? That said, the emerging attack surface management category focuses on internet-facing assets alone.

Dark Reading
JUNE 6, 2022
Randori’s attack-surface management software will be integrated into IBM Security QRadar extended detection and response (XDR) features.

NetSpi Executives
MARCH 5, 2024
Table of Contents What is External Attack Surface Management? The technology creates a comprehensive view of a company’s external assets by mapping the internet-facing attack surface to provide better insight into changes and where to focus the attention of security teams.
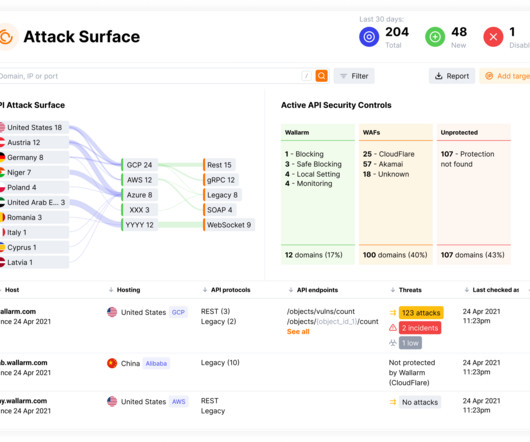
Security Boulevard
DECEMBER 4, 2023
The post Bolstering API Security: Introducing Wallarm’s API Attack Surface Management (AASM) appeared first on Wallarm. The post Bolstering API Security: Introducing Wallarm’s API Attack Surface Management (AASM) appeared first on Security Boulevard.

Security Boulevard
APRIL 26, 2023
Cavelo CEO James Mignacca and MDR pioneer and eSentire founder Eldon Sprickerhoff explore how attack surface management addresses cybersecurity’s visibility problem. The post Attack Surface Management (ASM) Solves Cybersecurity Visibility appeared first on Security Boulevard.

NetSpi Executives
MARCH 19, 2024
Attack surface sprawl is a growing challenge with 76% of organizations experiencing some type of cyberattack that started through the exploit of an unknown, unmanaged, or poorly managed internet-facing asset. How NetSPI Attack Surface Management covers gaps The beauty of ASM is its ability to uncover what’s unknown.

The Hacker News
JULY 17, 2023
For anyone ready to find an attack surface management (ASM) vendor, review these six questions before getting started to understand the key features to The hype around different security categories can make it difficult to discern features and capabilities from bias when researching new platforms.

Security Boulevard
DECEMBER 20, 2022
Cyber asset attack surface management helps businesses solve persistent asset visibility and vulnerability challenges. The post What is Cyber Asset Attack Surface Management? Here’s what you need to know. appeared first on Security Boulevard.

Security Boulevard
FEBRUARY 8, 2023
The average attack surface is growing rapidly, putting businesses at risk. Here are a few attack surface management tools to mitigate risk in 2023. The post The Top 3 Attack Surface Management Tools for 2023 appeared first on Security Boulevard.

SC Magazine
APRIL 22, 2021
Though the term Attack Surface Monitoring (ASM) doesn’t specifically refer to external threats, that’s what this market currently focuses on. In short, products in this category aim to catalogue and help manage an organization’s exposed assets. Attack Surface Management is a relatively new category.

Dark Reading
APRIL 26, 2022
Acquisition will add Internet-facing attack surface mapping and monitoring to Tenable's internal asset management products.

Trend Micro
APRIL 23, 2022
As organizations shift to the cloud in droves, their digital attack surface continues to rapidly expand. And with the number of threats rapidly increasing, security leaders need to enhance their attack surface risk management.

Digital Shadows
NOVEMBER 2, 2021
Recently we have been hearing plenty about External Attack Surface Management (EASM). The post Managing your External Attack Surface with SearchLight first appeared on Digital Shadows. While Digital Shadows focuses on digital risk protection.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content