How to Spot an Email Phishing Attempt at Work
Identity IQ
FEBRUARY 8, 2024
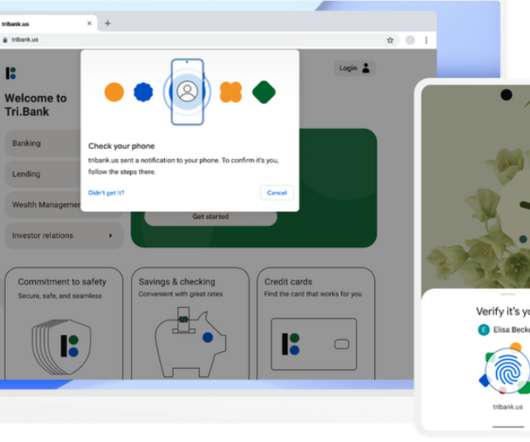
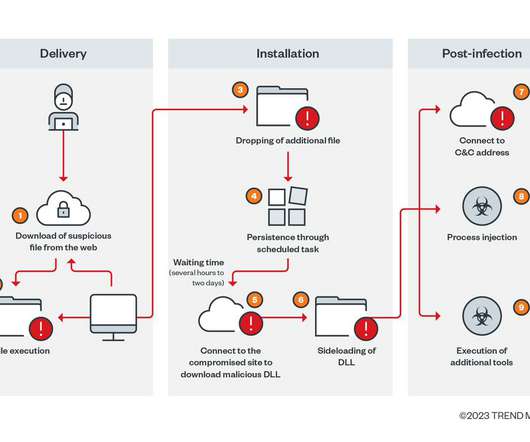
How to Spot an Email Phishing Attempt at Work IdentityIQ In the modern workplace, technology is just as common as the typical morning cup of coffee. Among these ever-present threats is phishing, which is a deceptively simple yet effective method cybercriminals use to compromise both business and personal accounts. What Is Phishing?
















































Let's personalize your content