Passwordless Protection: The Next Step in Zero Trust
Cisco Security
AUGUST 4, 2021
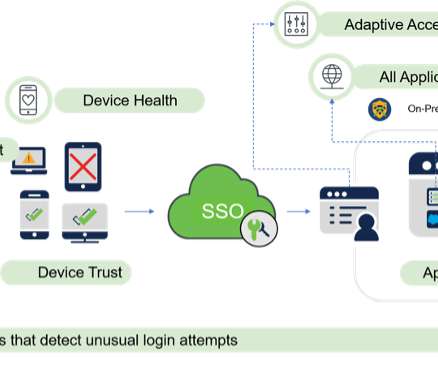
With the increasing threat landscape and recent workplace shifts to support remote users, many companies are deploying a Zero Trust security model to mitigate, detect, and respond to cyber risks across their environment. The Move to Passwordless. We’d love to hear what you think.



















Let's personalize your content