Calling Home, Get Your Callbacks Through RBI
Security Boulevard
JANUARY 17, 2024
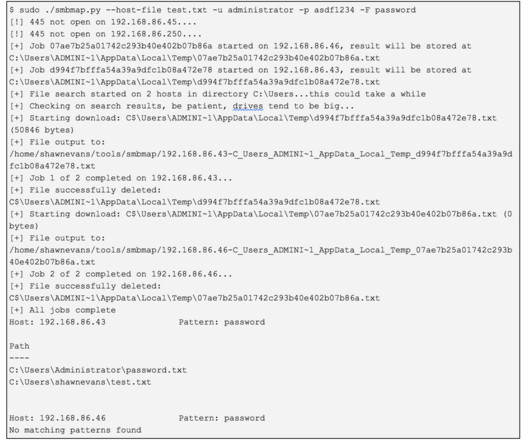
HTTP Authentication When attempting to have HTTP traffic egress an RBI security product, you must be prepared to authenticate to get out. It can automatically utilize stored NTLM credentials if available on a local system using the WinInet API if the proxy accepts it for basic or NTLM authentication.




















Let's personalize your content