Calling Home, Get Your Callbacks Through RBI
Security Boulevard
JANUARY 17, 2024
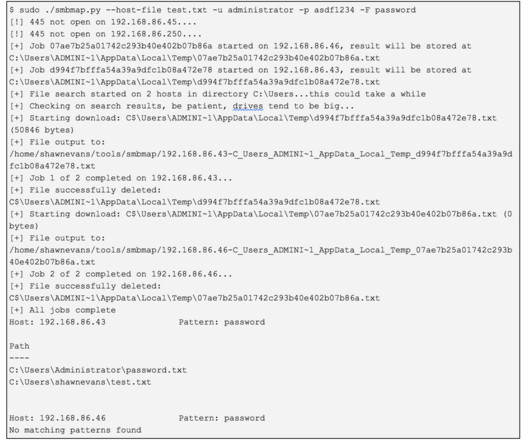
For example, Cloudflare Zero Trust blocks uploads and downloads of encrypted, password-protected files or files larger than 15MB by default because it cannot scan those files. Requiring user-supplied values such as passwords to access content increases the likelihood of successful payload detonation and delivery. pdf files, etc.,
























Let's personalize your content