Protecting Yourself from Identity Theft
Schneier on Security
MAY 6, 2019
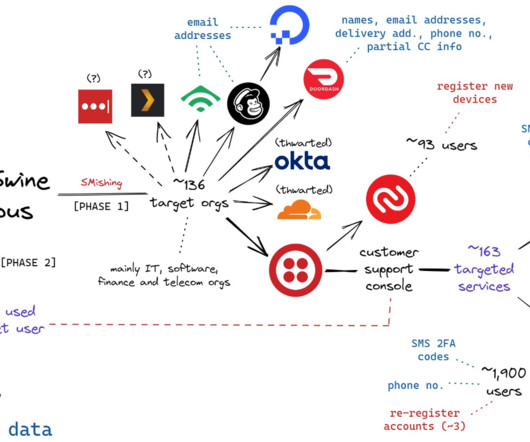
Ten years ago, I could have given you all sorts of advice about using encryption, not sending information over email, securing your web connections, and a host of other things -- but most of that doesn't matter anymore. Cybercriminals have your credit card information. They have your address and phone number.


















































Let's personalize your content