Akira Ransomware gang targets Cisco ASA without Multi-Factor Authentication
Security Affairs
AUGUST 31, 2023
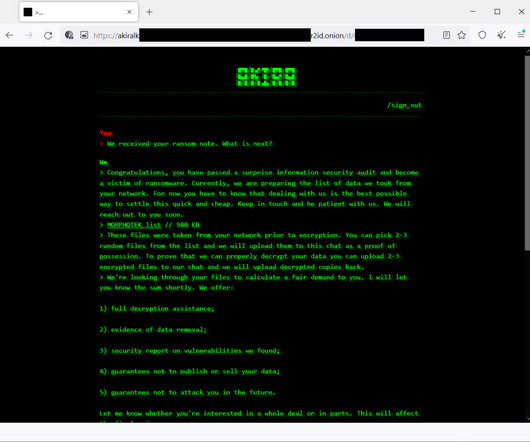
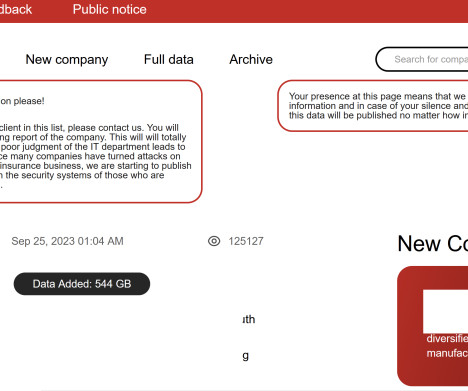
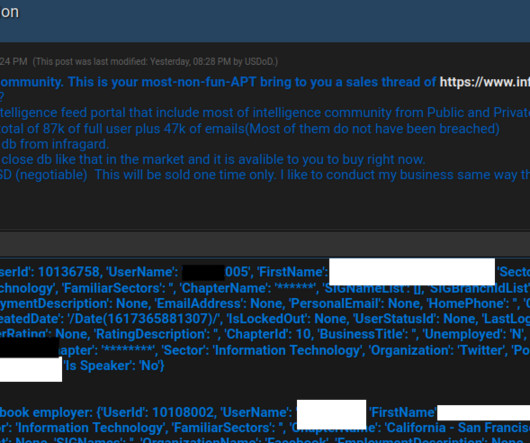
Cisco is aware of attacks conducted by Akira ransomware threat actors targeting Cisco ASA VPNs that are not configured for multi-factor authentication. “This highlights the importance of enabling multi-factor authentication (MFA) in VPN implementations. . ” reads a post published by Cisco PSIRT. 200 and 162.35.92[.]242












































Let's personalize your content