Why TOTP Won’t Cut It (And What to Consider Instead)
NetSpi Technical
JANUARY 18, 2024
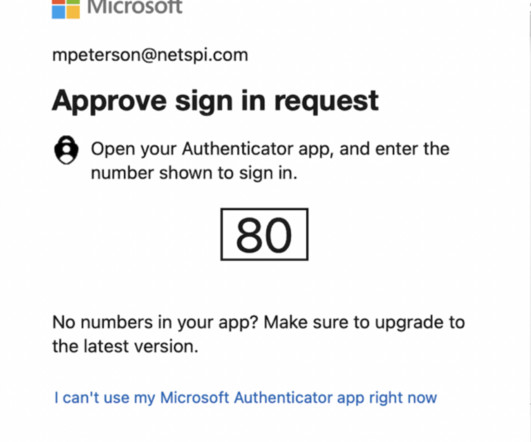
This article is co-authored by Gabe Rust. While TOTP was once an advancement in authorizing secure access, today it’s become a dated security measure that allows persistent threat actors to find exploitable gaps. If a product arbitrarily decides to implement 2FA, TOTP is likely high on the list of supported options.












Let's personalize your content