News alert: INE Security shares cyber hygiene guidance for small- and medium-sized businesses
The Last Watchdog
OCTOBER 23, 2024
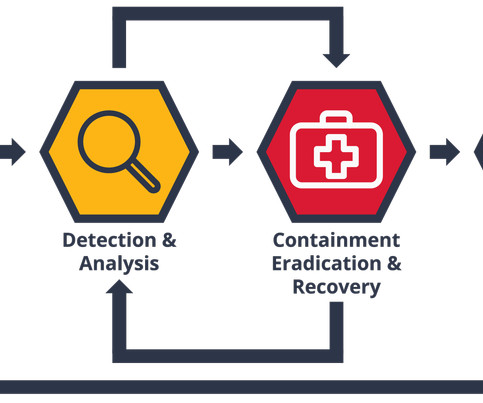
INE Security , a leading provider of cybersecurity training and certifications, today shared its cybersecurity training for cyber hygiene practices for small businesses, underscoring the critical role of continuous education in safeguarding digital assets. Many cyber attacks exploit vulnerabilities in outdated software.



















































Let's personalize your content