Don’t Wanna Pay Ransom Gangs? Test Your Backups.
Krebs on Security
JULY 19, 2021
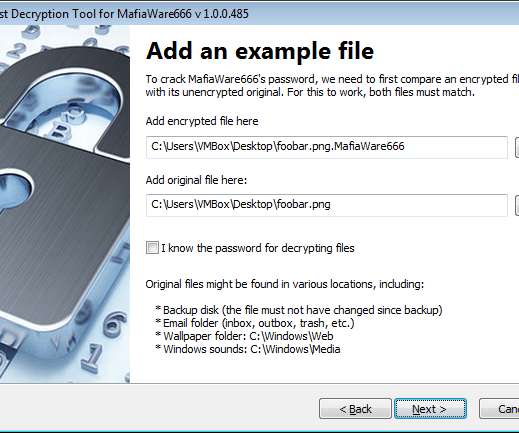
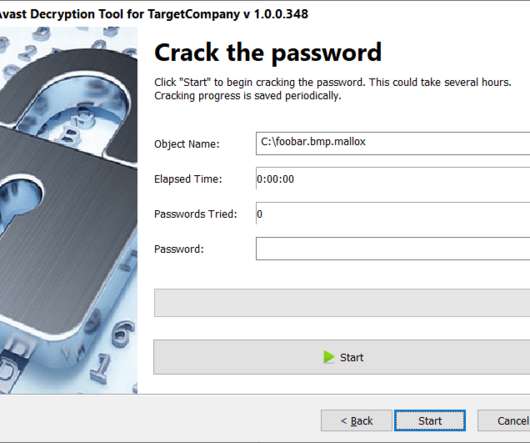
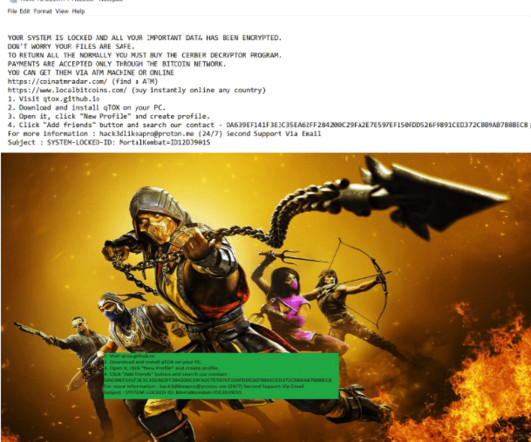
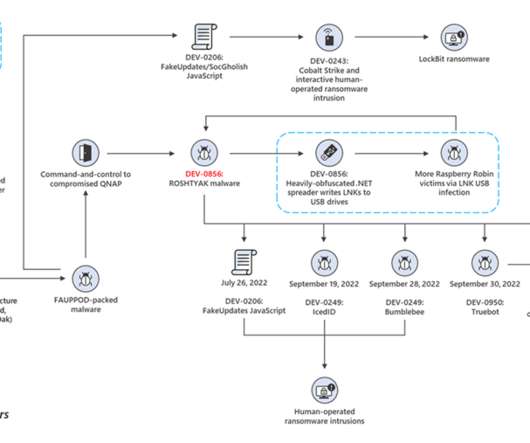
Browse the comments on virtually any story about a ransomware attack and you will almost surely encounter the view that the victim organization could have avoided paying their extortionists if only they’d had proper data backups. “It can be [that they] have 50 petabytes of backups … but it’s in a … facility 30 miles away.…









































Let's personalize your content