How Information Security Breaks The Classic IT Model
Security Boulevard
JUNE 26, 2022
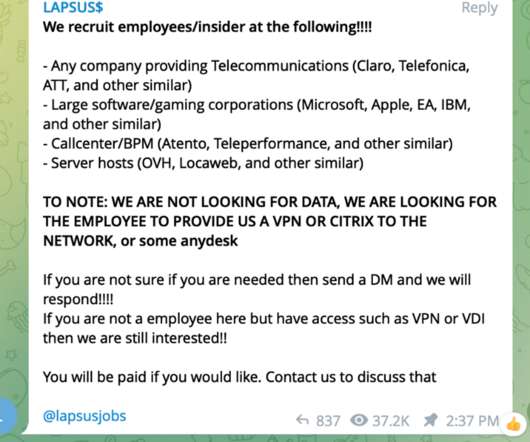
How Information Security Breaks The Classic IT Model. Many hacker groups will even approach social engineering to see if anyone in IT or SecOps knows if any layoffs are coming. How does information security fit into the producer/consumer model? The number of endpoints required to have EDR/XDR security.
































Let's personalize your content