Pegasus Project – how governments use Pegasus spyware against journalists
Security Affairs
JULY 19, 2021
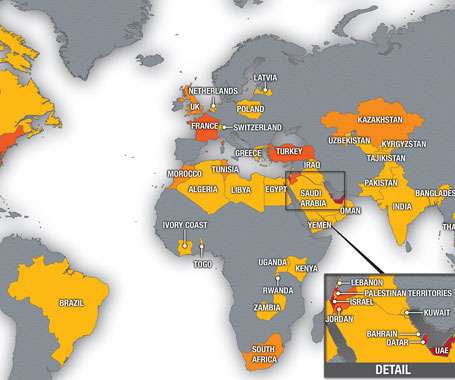
Pegasus Project investigation into the leak of 50,000 phone numbers of potential surveillance targets revealed the abuse of NSO Group’s spyware. Pegasus Project is the name of a large-scale investigation into the leak of 50,000 phone numbers of potential surveillance targets that revealed the abuse of NSO Group’s spyware.














Let's personalize your content