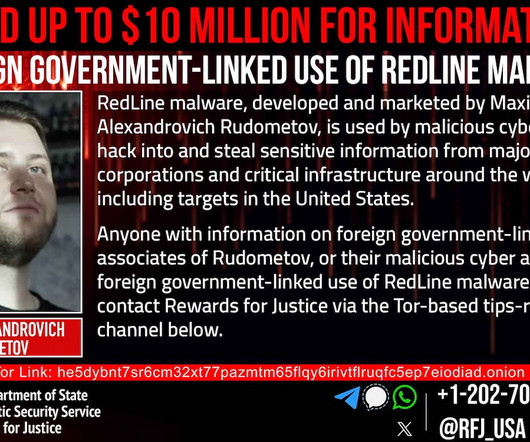
International law enforcement operation dismantled RedLine and Meta infostealers
Security Affairs
OCTOBER 29, 2024
Change passwords : After malware removal, update passwords for key accounts (email, banking, work, social media) and enable two-factor authentication. Monitor financial accounts : Check bank statements and report any suspicious transactions promptly. Use a password manager : Simplifies managing strong, unique passwords across accounts.





































Let's personalize your content