Detection as Code? No, Detection as COOKING!
Anton on Security
JUNE 3, 2022
It also resulted in this half-shallow / half-profound blog that relates detection to cooking and farming! Part 1 Key Questions Here on the blog I touched the subject of detection engineering quite a few times, yet I realize that many organizations prefer to rely on their security tool vendor content for threat detection.


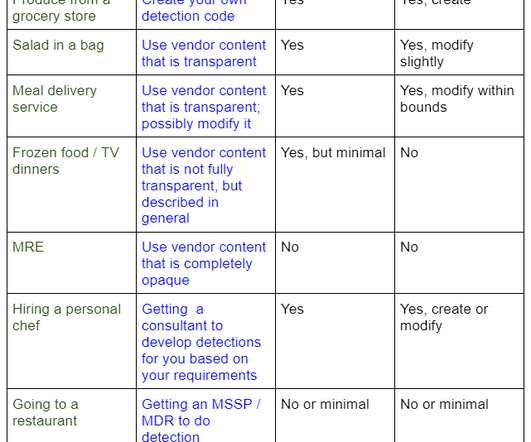
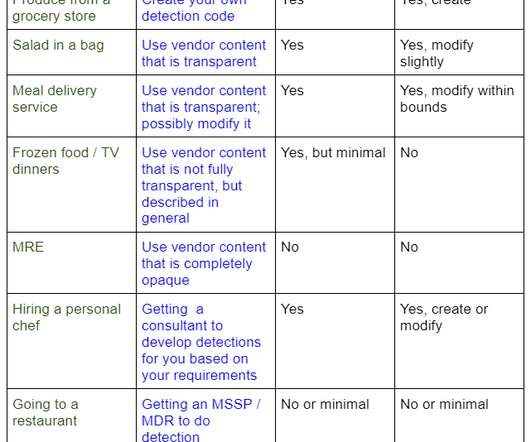







Let's personalize your content