NCSC on Good Architecture Diagrams
Adam Shostack
MAY 13, 2020
The UK’s National Computer Security Center has a blog post on Drawing good architecture diagrams.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Adam Shostack
MAY 13, 2020
The UK’s National Computer Security Center has a blog post on Drawing good architecture diagrams.
Security Boulevard
MARCH 25, 2022
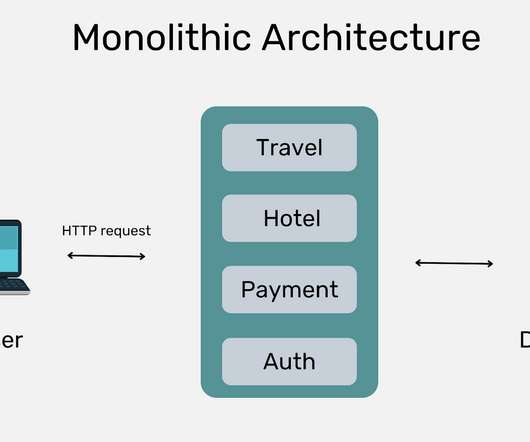
In this post we learn about monolithic vs microservices architectures and understand which to use and when. The post Monolithic vs. Microservices Architecture: Which Should I Use? The post Monolithic vs. Microservices Architecture: Which Should I Use? appeared first on Traceable App & API Security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
JUNE 16, 2021
This blog was written by an independent guest blogger. The post How Zero Trust architecture improves the organization’s network security appeared first on Cybersecurity Insiders. In the cybersecurity field, Zero Trust is becoming a widely used model. Nobody, including clients inside the firewall, should be trusted, per Zero Trust.

Security Boulevard
JULY 21, 2021
The post Webinar featuring IDC’s Mark Leary: Make your IT operations future-proof with the Branch of One architecture appeared first on ManageEngine Blog. The post Webinar featuring IDC’s Mark Leary: Make your IT operations future-proof with the Branch of One architecture appeared first on Security Boulevard.

Adam Shostack
OCTOBER 4, 2018
I last discussed this in “ Architectural Review and Threat Modeling “ ). Capitol Hill Seattle blog). ’ That’s human nature. Sometimes, it can be easier to learn from an analogy, and I’ll again go to physical buildings as a source. (I Now, Seattle has a very visible crisis of housing and homelessness.

McAfee
AUGUST 3, 2021
The rise of telemetry architectures, combined with cloud adoption and data as the “new perimeter,” pose new challenges to cybersecurity operations. It all begins with the build-up of an appropriate telemetry architecture, and McAfee Enterprise’s billion-sensor global telemetry is unmatched. Workflows are effortless to orchestrate.

Heimadal Security
MARCH 12, 2021
The post The Security Checklist for Designing Asset Management System Architectures appeared first on Heimdal Security Blog.

Security Boulevard
SEPTEMBER 17, 2022
Keep reading for suggestions on how to build a zero-trust security architecture with …. How to Build a Zero Trust Security Architecture with Your Technology Read More ». The post How to Build a Zero Trust Security Architecture with Your Technology appeared first on TechSpective.

Security Boulevard
OCTOBER 6, 2022
How Dynamic Authorization Enables a Zero Trust Architecture. As PlainID’s Gal Helemski mentioned in her presentation, centralized management of all identities – human and machine identities – with decentralized enforcement is the key for enabling a Zero Trust architecture. brooke.crothers. Thu, 10/06/2022 - 11:30. UTM Medium.

Security Boulevard
DECEMBER 15, 2022
The post Multi-Cloud Architectures Driving Changes for Compliance and Audit Requirements appeared first on Netography. The post Multi-Cloud Architectures Driving Changes for Compliance and Audit Requirements appeared first on Security Boulevard.
Cisco Security
DECEMBER 13, 2021
It makes architectures more scalable, in part by removing the need for source network address translation (SNAT) in the traffic path. Figure 1 below shows a scalable architecture for protecting ingress traffic using Cisco Secure Firewall and AWS Gateway Load Balancer. Figure 3 shows centralized security deployment architecture.

CyberSecurity Insiders
DECEMBER 21, 2021
This blog was written by an independent guest blogger. The post How to evolve your organization into a data-centric security architecture appeared first on Cybersecurity Insiders. Older security models focused on network infrastructure and hardware security controls while data-centric security concentrates on the data itself.

The Last Watchdog
OCTOBER 23, 2023
Splunk’s inability to migrate to a modern cloud-native architecture makes it difficult to take advantage of these cost-saving benefits or implement advanced data science use cases critical for threat detection. Influxes of data ingestion and the flat architecture of data lakes have led to difficulties in extracting value from repositories.

Duo's Security Blog
DECEMBER 6, 2022
Start your passwordless journey today While there are several ways to start your journey to a passwordless future , I hope that this article has helped to understand the fundamental building blocks for a passwordless architecture.
Security Boulevard
APRIL 13, 2024
This evaluation involves scrutinizing the code, architecture, and deployment environment to assess the security posture of the applications. appeared first on Kratikal Blogs. Flaws in web application coding accounted for 72% of the identified vulnerabilities. The post What is Web Application Security Testing?
Cisco Security
MARCH 1, 2024
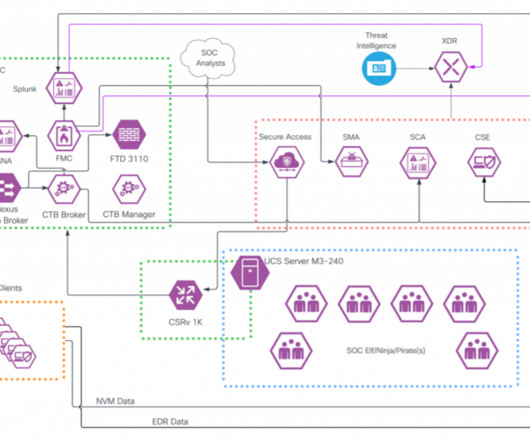
2 SOC Architecture. 2 Cisco Secure Access Enables ZTNA for SOC… Read more on Cisco Blogs This year, the team was tapped to build a similar team to support the Cisco Live Melbourne 2023 conference. Executive Summary. 1 The Team… 2 Team Leaders. 2 Core Infrastructure and Threat Hunting. 2 Threat Hunting. 2 Build and Operation.

Security Boulevard
OCTOBER 4, 2021
To echo a famous Russian proverb, "trust but verify," it's not enough to implement a zero trust architecture. It’s not enough to deploy a zero trust architecture. It’s not enough to deploy a zero trust architecture. Continuous testing is the only way to achieve real cybersecurity readiness. The post “Zero Trust But Validate.”

Security Boulevard
FEBRUARY 22, 2022
Microservice architecture is one of the hot topics nowadays by increasing the need of agility to meet customers’ expectations. are the main benefits of microservice architecture. Besides these benefits, microservice architecture has its own unique and hard to solve challenges.

Thales Cloud Protection & Licensing
MARCH 10, 2021
Guest Blog: TalkingTrust. There are many different layers of security involved in protecting connected devices, and security should start with a high-level architecture of the IoT stack and connected ecosystem. What’s driving the security of IoT? Thu, 03/11/2021 - 07:39. The Urgency for Security in a Connected World. Edge Devices.

Security Boulevard
MAY 2, 2024
Chris Clements, VP of Solutions Architecture at CISO Global “Hey Alexa, are you stealing my company’s data?” In an age where manufacturers have decided that just about every device needs to be “smart,” it’s becoming difficult to avoid the data collection and privacy invasion that are often baked into these devices.

Heimadal Security
MAY 26, 2023
Given the rise of remote work, cloud computing, and increasingly complex cyber threats, conventional network architectures and perimeter-based security measures are no longer enough. appeared first on Heimdal Security Blog. Zero Trust Network Access Explained.

Security Boulevard
AUGUST 1, 2022
Hybrid architectures had grown too complex to be able to provide adequate defense, resulting in new larger threat surfaces. The post This was H1 2022 – Part 1 – The Fight Against Cybercrime appeared first on Radware Blog. Cyber crime was too widespread and heavily resourced.

Heimadal Security
MARCH 11, 2022
The SaaS architecture allows companies to focus on their core business while the third-party provider focuses on managing the security. The post SaaS Security: How to Protect Your Enterprise in the Cloud appeared first on Heimdal Security Blog. What Is Software as a Service? Software as a service […].

Security Boulevard
FEBRUARY 2, 2023
New architectures such as multi-cloud and microservices have made consistent security controls […] The post Software Supply Chain Risks for Low- and No-Code Application Development appeared first on Radware Blog. This can happen through backdoors planted in software updates, as seen in incidents like SolarWinds and Kaseya.

Heimadal Security
JANUARY 9, 2023
Although container-based architecture comes with a series of advantages: portability, lightweight, easy maintenance, and scalability, it also rises specific security challenges. The post Best Practices Check List for Flawless Container Security appeared first on Heimdal Security Blog. Unlike running […].

CyberSecurity Insiders
MAY 30, 2023
Introduction Today you look at the Global/Multi-site Enterprise Security Architecture of an organization and see a myriad of concerns. Global/Multi-Site Enterprise Architecture Many organizations are using Global/Multi-site with dated technology spread throughout data centers and networks mixed in with some newer technologies.

Security Boulevard
JANUARY 22, 2024
Keeping architectures and systems secure and compliant can seem overwhelming even for today’s most skilled teams. In the modern landscape of cybersecurity risk management, one uncomfortable truth is clear — managing cyber risk across the enterprise is harder than ever.

Heimadal Security
MARCH 15, 2023
The company provides CNC machining, laser cutting and waterjet cutting services for the aerospace, architectural, defense, marine, military, medical and mining industries. The ransomware […] The post LockBit Ransomware Claims to Have Stolen SpaceX Data from One of Its Contractors appeared first on Heimdal Security Blog.

Krebs on Security
DECEMBER 1, 2022
29, roughly the same time Pyle published a blog post about his findings , ConnectWise issued an advisory warning users to be on guard against a new round email phishing attempts that mimic legitimate email alerts the company sends when it detects unusual activity on a customer account.

Heimadal Security
OCTOBER 24, 2022
Nowadays, the traditional on-site computing architecture is moved to remote facilities that are normally under the management of a third party as enterprises convert, entirely or in part, to cloud-based services. The post DNS Best Practices: A Quick Guide for Organizations appeared first on Heimdal Security Blog.

Heimadal Security
NOVEMBER 3, 2021
MITRE has released a list of this year’s most hazardous programming, design, and architecture security issues affecting hardware. Vulnerabilities in hardware programming, design, or architecture can all lead to exploitable flaws leaving systems vulnerable to cyberattacks.

Veracode Security
SEPTEMBER 25, 2023
This blog is the fifth and final part of the series, and it will teach you to handle credentials and secrets management best practices for securing cloud-native applications. In the past, with legacy application architectures, this was a bit more manual and arduous. Every organization has their way of managing credentials.

Heimadal Security
JANUARY 21, 2022
TrickBot appeared in 2016, replicating parts of Dyre’s malware while preserving its banking credential harvesting and web inject architecture. The post Diavol Ransomware Appears to Have Connections with TrickBot appeared first on Heimdal Security Blog. TrickBot has evolved into a malware […].

Heimadal Security
MAY 13, 2022
Plugin architecture and a template system, which are both referred to as Themes inside WordPress, are both included as features. The post WordPress Websites Files and Databases Injected with Malicious JavaScript appeared first on Heimdal Security Blog. It is built in PHP, and it can be combined with either a MySQL or MariaDB database.
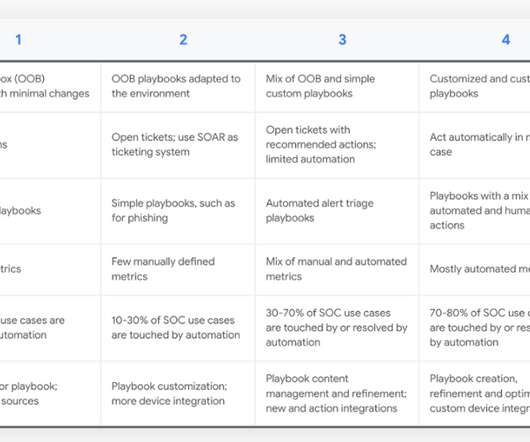
Anton on Security
JUNE 17, 2022
Originally written for a new Chronicle blog. Thanks to Google SOAR Solution Architecture Manager Oleg Siminel , and others from the Siemplify field team, for their support here. My favorite approach has been a maturity model, vaguely modeled on the CMM approach.

Heimadal Security
DECEMBER 17, 2021
The previously retired Phorpiex botnet has resurfaced with new peer-to-peer command and control architecture, making the virus more difficult to destroy. The post Phorpiex Botnet Is Becoming Harder to Disrupt appeared first on Heimdal Security Blog.

Heimadal Security
JUNE 17, 2022
The XACML standard defines not only a language for access control policies but also a language for request and response as well as a reference architecture. The post The Complete Guide to XACML appeared first on Heimdal Security Blog. Access control policies may be expressed via the […].

Heimadal Security
DECEMBER 6, 2022
The transformation is accidental, and it is caused by poor architecture and programming flaws. The post Cryptonite Ransomware Toolkit Unintentionally Transforms into a Wiper appeared first on Heimdal Security Blog. Cryptonite open-source toolkit has been observed turning itself into a data wiper.

Thales Cloud Protection & Licensing
NOVEMBER 14, 2018
His experience spans the software development life cycle including pre-sales engineering, architecture, design, development, test, and solution implementation. The post Guest Blog: Why it’s Critical to Orchestrate PKI Keys for IoT appeared first on Data Security Blog | Thales eSecurity.

Heimadal Security
NOVEMBER 9, 2021
Ransomware-as-a-Service is an illegal ‘parent-affiliate(s)’ business architecture in which operators (i.e., The post A Tough Week for REvil Ransomware appeared first on Heimdal Security Blog. malicious software owner and/or creator) […].
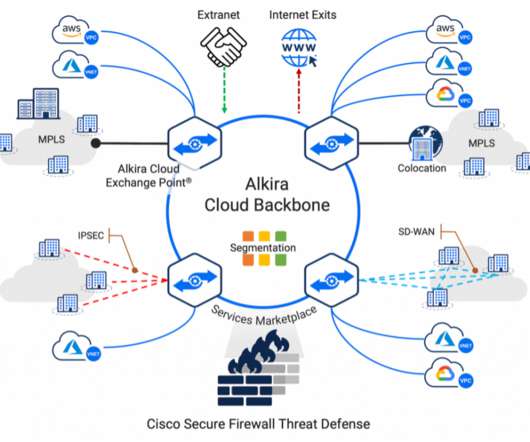
Cisco Security
FEBRUARY 2, 2023
These applications/workloads move to, and reside in multi-cloud architecture, adding complexity to connectivity, visibility, and control. In today’s security climate, NetOps and SecOps teams are witnessing increased attack surface area as applications and workloads move far beyond the boundaries of their data center.
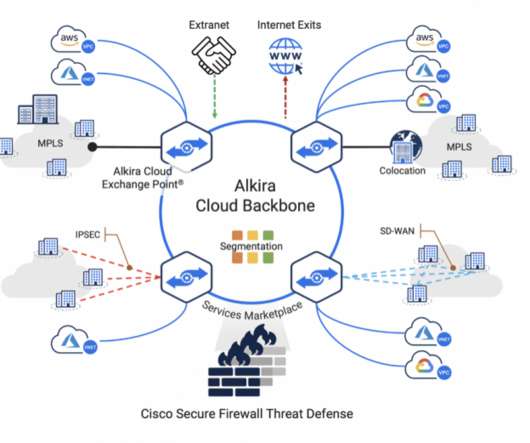
Cisco Security
DECEMBER 14, 2021
These applications/workloads move to, and reside in, multicloud architecture, adding complexity to connectivity, visibility, and control. Benefits of this integrated architecture include: . Auto-scaling: Cisco Secure Firewall provides a flexible architecture that can autoscale with the network load. Resources: .
CSO Magazine
AUGUST 26, 2022
An initial probe of the incident has revealed no evidence that customer data or encrypted password vaults were accessed by the intruder, CEO Karim Toubba stated in a company blog post. To read this article in full, please click here

SecureWorld News
DECEMBER 21, 2023
A trend of non-vetted content Not long into the fall 2023 semester, students began to cite blogs and vendor materials that made sense but were partly or entirely incorrect. In this case, students needed to learn about the evolution of operating system architecture. For my own blogs, I’ve reached out to known experts to review them. (In
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content