Free and Downloadable Account Management Policy Template
Heimadal Security
APRIL 23, 2024
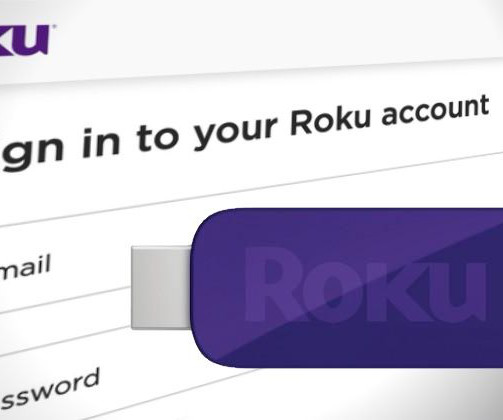
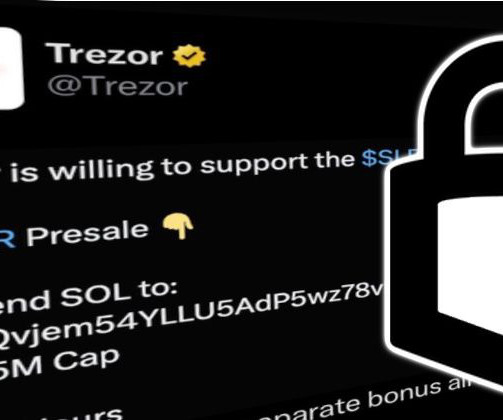
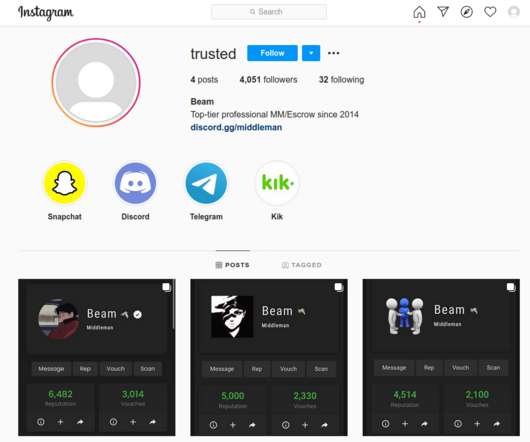
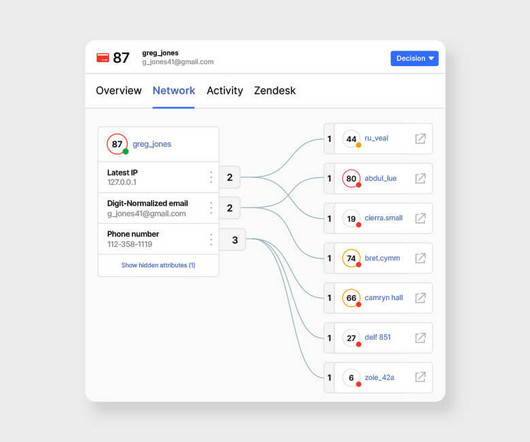
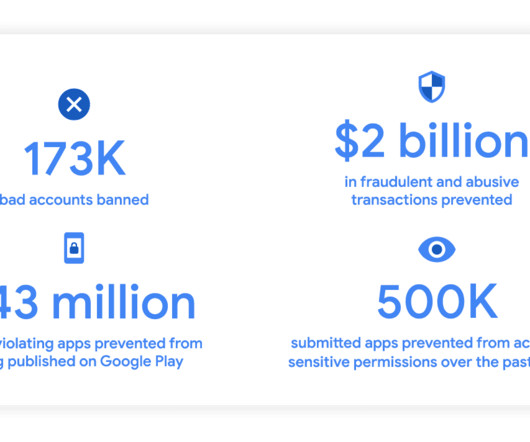
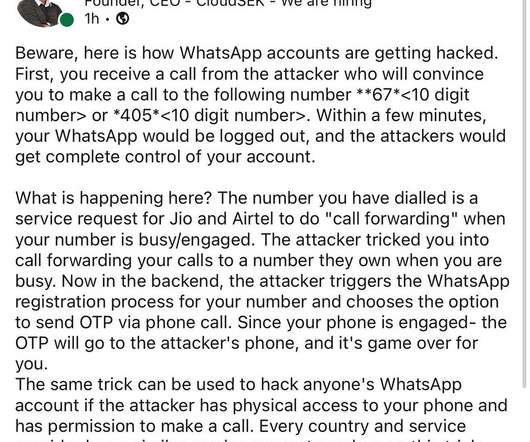
Managing user accounts and ensuring the security of data and information systems are crucial for any business. To assist organizations in this task, we offer a comprehensive Account Management Policy Template designed to streamline the process of account creation, maintenance, and termination.










































Let's personalize your content