Ukraine’s Response to Cyber Threats a Model in DDoS Prevention
Security Boulevard
NOVEMBER 7, 2022
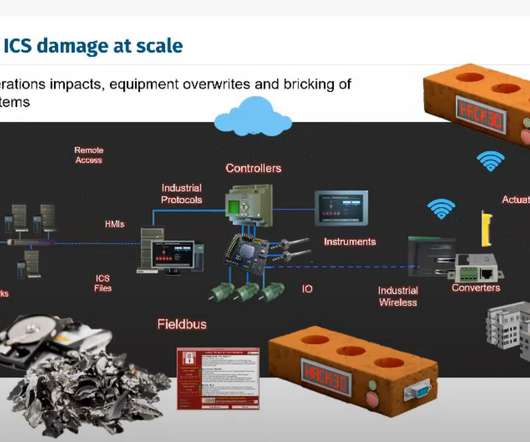
With the disruption, loss of life and heartbreaking images that the Russia-Ukraine conflict has produced, it is easy to overlook what it has meant to the cyber threat landscape. The post Ukraine’s Response to Cyber Threats a Model in DDoS Prevention appeared first on Radware Blog. Even threat actors have taken sides.












Let's personalize your content