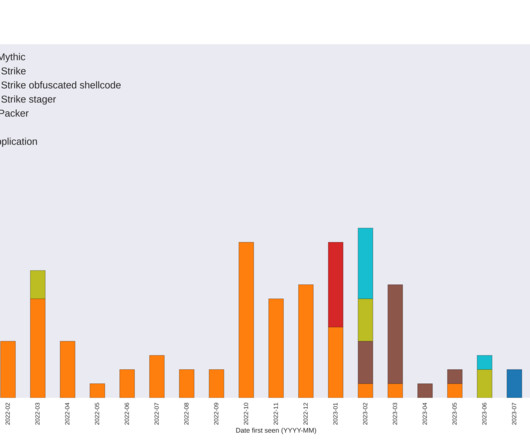
Emotet Is Dropping Cobalt Strike
Heimadal Security
DECEMBER 8, 2021
Emotet is a virus infection that is propagated by spam email attachments that contain malicious Word or Excel documents. These documents utilize macros to download and install the Emotet Trojan on a victim’s computer, which is then used to steal email and install further malware.













Let's personalize your content