A consumer-grade spyware app found in check-in systems of 3 US hotels
Security Affairs
MAY 22, 2024
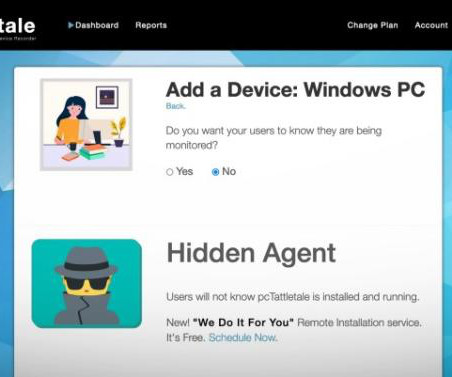
A researcher discovered a consumer-grade spyware app on the check-in systems of at least three Wyndham hotels across the US. The security researcher Eric Daigle discovered a commercial spyware app, called pcTattletale, on the check-in systems of at least three Wyndham hotels across the US, TechCrunch first reported.














Let's personalize your content