Secure your data throughout its lifecycle with End-to-End Data Protection
Thales Cloud Protection & Licensing
JUNE 18, 2025
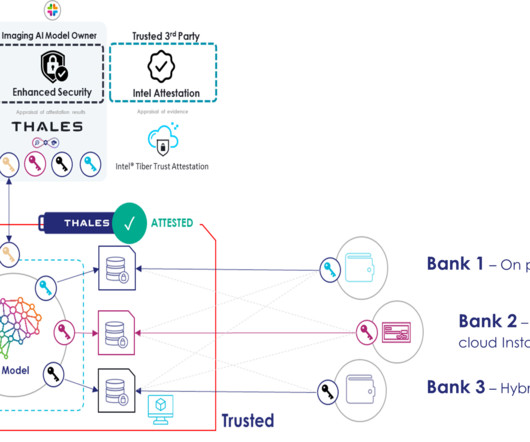
By combining robust encryption, trusted execution environments, and support from Intel Tiber Trust Authority and major cloud providers, this solution brings continuous, verifiable protection to even the most sensitive workloads. With E2EDP: Data is encrypted on-prem and stays protected throughout its journey.



















Let's personalize your content