Who Does What In Cloud Threat Detection?
Anton on Security
FEBRUARY 8, 2022
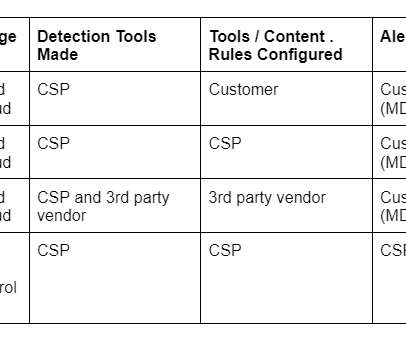
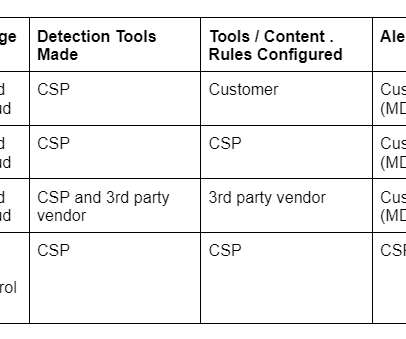
This post is a somewhat random exploration of the cloud shared responsibility model relationship to cloud threat detection. Funny enough, some popular shared responsibility model visuals don’t even include detection, response or security operations. Related blogs: “Why is Threat Detection Hard?” “On















Let's personalize your content