Phishing Campaign Used Morse Code to Evade Detection: Microsoft
eSecurity Planet
AUGUST 16, 2021
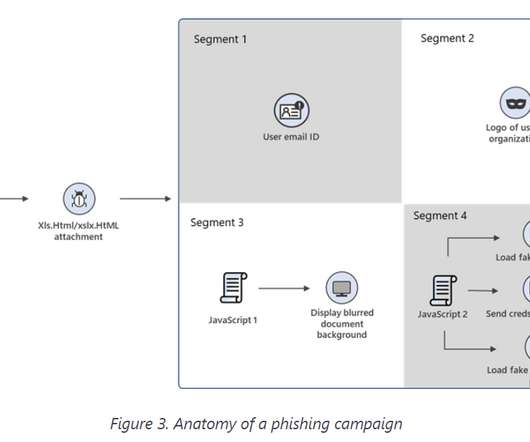
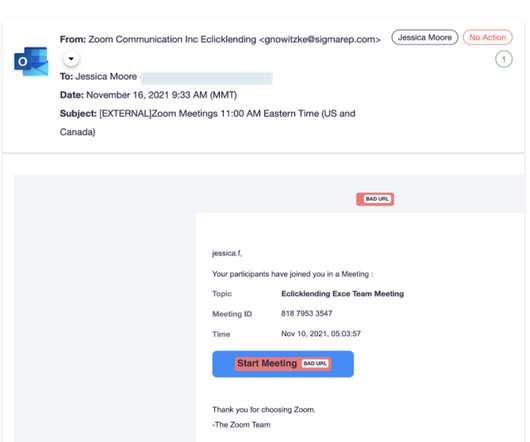
A phishing campaign that Microsoft security researchers have been tracking for about a year highlights not only the ongoing success of social engineering efforts by hackers to compromise systems, but also the extent to which the bad actors will go to cover their tracks while stealing user credentials.



























Let's personalize your content