The role of cybersecurity in financial institutions -protecting against evolving threats
CyberSecurity Insiders
JUNE 1, 2023
Cybersecurity is practice of protecting information technology (IT) infrastructure assets such as computers, networks, mobile devices, servers, hardware, software, and data (personal & financial) against attacks, breaches and unauthorised access. for malicious actions by hiding as a reliable person in electronic interaction.







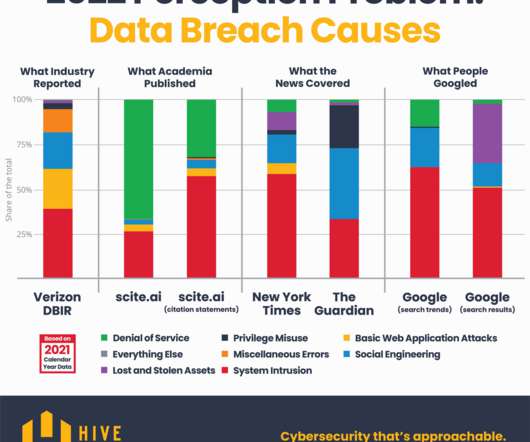
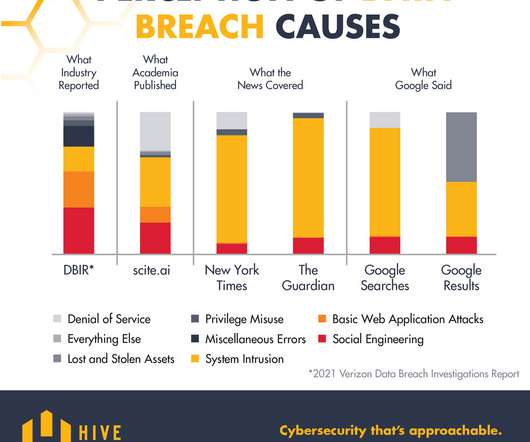

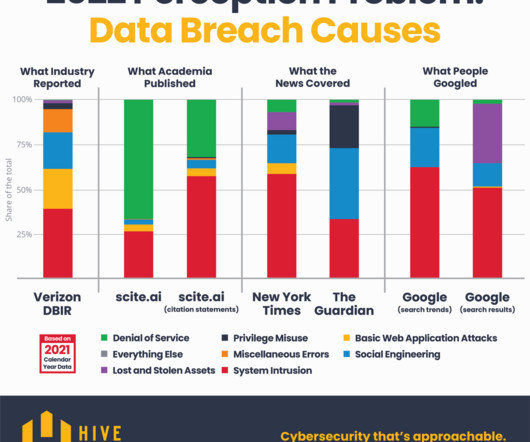








Let's personalize your content