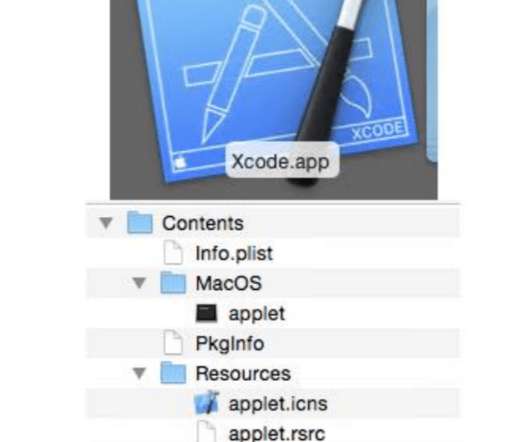
XCSSET Mac spyware spreads via Xcode Projects
Security Affairs
AUGUST 15, 2020
The malware also implements ransomware behavior, it is able to encrypt files and display a ransom note. This behavior allows the malicious code to replace cryptocurrency addresses, and steal credentials for online services (amoCRM, Apple ID, Google, Paypal, SIPMarket, and Yandex) and payment card information from the Apple Store.


















Let's personalize your content