Octo Tempest cybercriminal group is "a growing concern"—Microsoft
Malwarebytes
OCTOBER 27, 2023
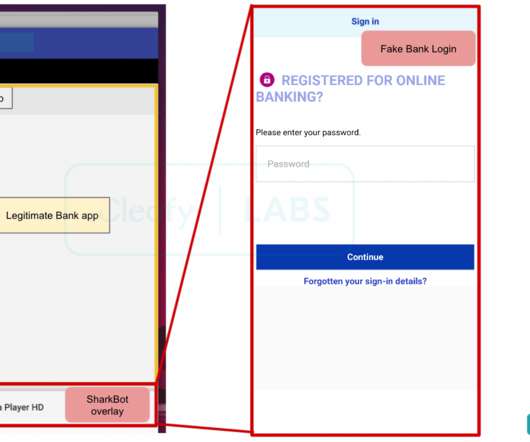
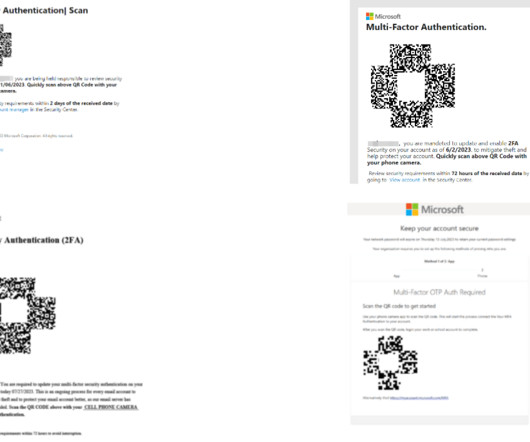
Octo Tempest is believed to be a group of native English speaking cybercriminals that uses social engineering campaigns to compromise organizations all over the world. This can be done in a number of ways, but the most common ones involve social engineering attacks on the victim's carrier.



















Let's personalize your content