The Retail Data Threat Environment and Why CIAM is a Key Cornerstone to Better Cybersecurity.
Thales Cloud Protection & Licensing
MAY 10, 2023
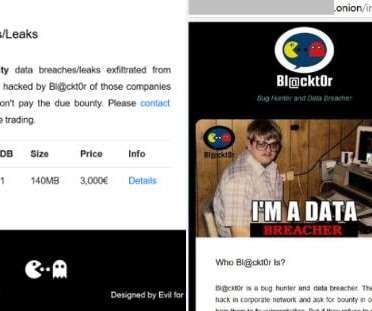
The Retail Data Threat Environment and Why CIAM is a Key Cornerstone to Better Cybersecurity. madhav Thu, 05/11/2023 - 06:06 The retail landscape has changed significantly. Customers should be aware of the existing threats, while retailers must understand the risks associated with poor management of customer identities.


























Let's personalize your content