Data Privacy and Security: It Takes Two to Tango
Thales Cloud Protection & Licensing
JANUARY 24, 2022
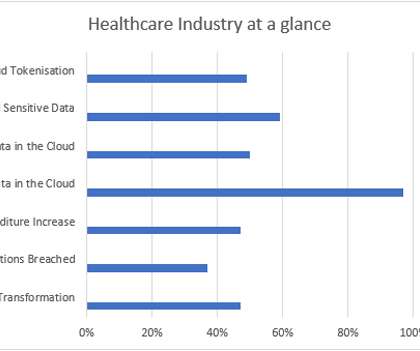
It is important to understand that nowadays almost all our data – including our personal data, like banking information, medical records, and personal emails – are stored and processed in the cloud. However, with technology innovation comes new risks, security challenges and threats. million on average.












Let's personalize your content