GUEST ESSAY: How ‘DPIAs” — data privacy impact assessments — can lead SMBs to compliance
The Last Watchdog
JANUARY 9, 2023
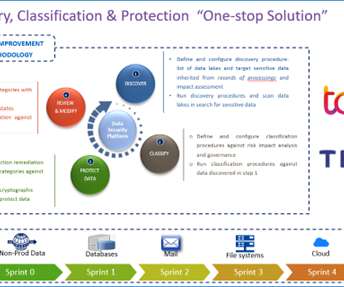
As the world becomes more digital and connected, it is no surprise that data privacy and security is a growing concern for small to medium sized businesses — SMBs. Related: GDPR sets new course for data privacy. Let’s look at some of the challenges faced by SMBs in today’s data privacy landscape.


















Let's personalize your content