Protect Your Business With This Seamless Firewall — Now $150 Off
Tech Republic Security
MARCH 27, 2024
DNS FireWall is an intuitive security app built to protect you and your business from malware, phishing, botnets and more security threats.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Malwarebytes
JUNE 1, 2022
If you’re an SMB, chances are that you’re already well-aware of the fact that cyber threats can wreak havoc on your business. That’s where DNS filtering comes in. But first, DNS in a nutshell. So normally, every time your customer types in your web address, their computer makes a request to a DNS server.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
OCTOBER 2, 2023
Phishing Threats Are Increasing in Scale and Sophistication Phishing remains one of the most dangerous and widespread cybersecurity threats. Phishing is now the most common initial attack vector, overtaking stolen or compromised credentials. Phishing attacks are becoming more difficult to detect.

Security Boulevard
JULY 9, 2024
Defense in depth and operational resiliency are the future for organizations that want to survive in the new world of cyber threats. Operational resiliency necessitates intelligence, visibility, and confidence: the three foundational pillars of protective DNS (PDNS). How and Why Do Cyber Attacks Happen?

Security Boulevard
AUGUST 7, 2024
HYAS Protect protective DNS uses advanced data analytics to proactively block cyber threats, a feature unavailable in legacy systems relying on static DNS filtering. AV-TEST , one of the cybersecurity industry’s most trusted evaluators, rates HYAS as the most effective protective DNS solution on the market.
Security Boulevard
APRIL 4, 2025
Increase monitoring and logging of DNS and network traffic; and set up fast flux alert mechanisms. Share fast flux detection indicators, such as domains and IP addresses, with partners and threat intelligence communities via, for example, the U.S.s Automated Indicator Sharing and Australias Cyber Threat Intelligence Sharing Platform.

Security Boulevard
FEBRUARY 20, 2025
DNS attacks can lead to data breaches, phishing, and service disruptions. Learn about common types of DNS attacks and how to protect your domain from cyber threats. The post Types of DNS Attacks: How They Work & How to Stay Protected appeared first on Security Boulevard.

Security Boulevard
MARCH 18, 2025
Cyber threats are growing in sophistication, and adversaries are continually evolving their methods, targeting businesses, governments, and individuals with precision. It consolidates multiple layers of information and correlates them to deliver a contextualized understanding of cyber threats.
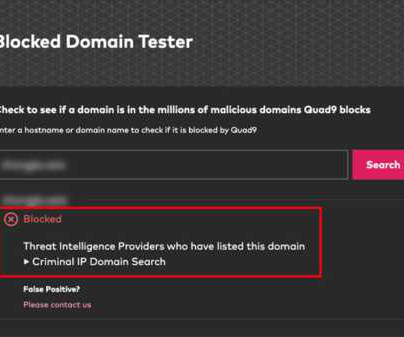
The Last Watchdog
MAY 13, 2024
May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users.
Security Boulevard
FEBRUARY 23, 2023
Thankfully, nearly all malware depends on DNS at some point in their kill chain, making the protocol a critical vector for shutting down these threats. Some of the common forms these DNS-based attacks can take include: DNS spoofing: A malicious actor alters DNS records to redirect traffic to a fake website or server.

Webroot
MAY 6, 2024
As we navigate through 2024, the cyber threat landscape continues to evolve, bringing new challenges for both businesses and individual consumers. The latest OpenText Threat Report provides insight into these changes, offering vital insights that help us prepare and protect ourselves against emerging threats.

Security Boulevard
APRIL 8, 2025
Attackers use phishing, pretexting, and baiting to gain access or information. Defenders use this knowledge to create security awareness training programs and conduct phishing simulations. Social Engineering Tactics: These tactics exploit human psychology to manipulate individuals.

Security Boulevard
JUNE 20, 2024
The financial sector is a prime target for cyber attacks. Financial organizations and their customers and clients feel the fallout of major ransomware and phishing campaigns more than ever, and there’s often more at stake. With the number of cyber threats on the rise, no sector is truly safe from serious fallout.

SecureWorld News
MAY 16, 2024
Popular services include receiving actionable intelligence on threats targeting their systems and leveraging the NSA's leading malware reverse-engineering skills to remove cyber threats after breaches. Companies with active DoD contracts are encouraged to learn more about the CCC and enroll in NSA's DIB Cybersecurity services.

Security Boulevard
MARCH 6, 2024
Traditionally, cybersecurity has been a reactive game: We respond to cyber threats as they arise, analyze the incidents, add pertinent information to “deny lists”, and update stakeholders on “what happened.” That's where technologies like protective DNS come in. It may sound difficult, but change always sounds hard at first.

Webroot
MAY 25, 2021
Yet, faced with modern cyber threats, that seems like a pretty impossible goal, particularly as many attacks are designed to operate under the radar, evading detection for weeks or months at a time. Phishing and business email compromise are still top security concerns , but they’re surprisingly preventable at the end user level.

Webroot
NOVEMBER 7, 2022
Meanwhile, the global rise in sophisticated ransomware threats and geo-political tensions are escalating cyber threats. Of these SMBs, 31% conduct security awareness trainings only once a year; 10% only if an employee fails a phishing test. The looming recession and inflation have created financial uncertainty.

Hacker's King
OCTOBER 12, 2024
Maltego works by using "transforms" to extract data from a range of online sources such as DNS records, whois databases, social media, and web pages. The tool is particularly useful when identifying potential targets or email addresses for phishing campaigns. Why Use Maltego? Why Use theHarvester?

CyberSecurity Insiders
JUNE 29, 2023
Executive summary Credential harvesting is a technique that hackers use to gain unauthorized access to legitimate credentials using a variety of strategies, tactics, and techniques such as phishing and DNS poisoning. According to recent research , phishing assaults targeted credential harvesting in 71.5% of cases in 2020.

Security Boulevard
MAY 17, 2024
HYAS Protect protective DNS includes a user-friendly interface and four core deployment methods. Organizations of any size can monitor traffic with HYAS Protect’s cloud-based DNS resolver. DNS data from HYAS Protect allows organizations to identify their riskiest users and prioritize proactive security measures.

IT Security Guru
MARCH 17, 2023
Sometimes, cyber threats are closer to home, making them all the more surprising (and frustrating) for many organizations. They’re called insider threats, and you need to pay special attention to ensure you – and your data – don’t fall victim. Yet, cybercrime doesn’t always look like a scene from a Hollywood movie.

Security Boulevard
JUNE 22, 2023
Securing SMB Success: The Indispensable Role of Protective DNS Cyber attacks pose as much risk to small and medium-sized businesses (SMBs) as they do to large organizations — if not more. Implementing a Domain Name Service (DNS) security solution is the most efficient way to protect your business against a wide variety of attacks.

Security Boulevard
FEBRUARY 7, 2024
Germany-based independent security evaluators AV-TEST found that HYAS Protect Protective DNS is the most effective operational resiliency solution on the market today to drive business continuity and continued operations. While businesses’ entire security stacks do matter, it’s impossible to stop all nefarious activity beforehand.

eSecurity Planet
NOVEMBER 18, 2021
Phishing scams use it to compromise networks. They spot unwanted traffic such as spam, phishing expeditions, malware, and scams. A good email gateway will contain most of the following features: Identify and filter spam, viruses, phishing and malware from URLs or attachments. Key Features of Secure Email Gateways.

Security Boulevard
SEPTEMBER 10, 2024
One major managed service provider (MSP) which we’ll call “MSP Global” offers security operations center as-a-Service (SOCaaS) and cyber threat hunting, detection, and response for clients in more than 150 countries and territories. Q: What drove MSP Global to consider HYAS as a threat intelligence and incident response solution?
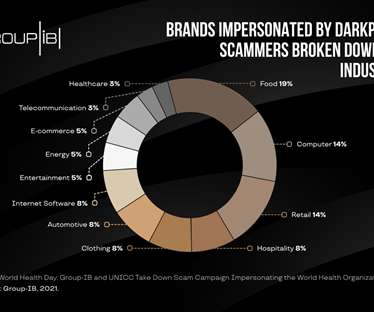
Security Affairs
APRIL 30, 2021
Upon detection, Group-IB’s Digital Risk Protection reached out UNICC’s Common Secure team as a trusted contact for cyber threat intelligence matters within the UN ecosystem, to assure that proper contacts within WHO were aware of the scam. In the worst-case scenarios, users would end up on a malicious or a phishing website.

eSecurity Planet
SEPTEMBER 29, 2021
Recent research by Positive Technologies looked at the cyber threat landscape during Q2 2021 and found that ransomware attacks reached “stratospheric” levels, accounting for 69% of all malware attacks, a huge jump from 39% in Q2 2020. Detection to stop sophisticated cyber threats. DNS filtering.

Security Boulevard
JULY 30, 2024
The internet is a vast landscape filled with potential threats, from phishing sites to malware. This helps safeguard your company’s sensitive information and defends against data breaches, ransomware attacks, and other disruptive cyber incidents. Why is content filtering so essential?

Security Boulevard
MAY 20, 2024
Weekly Threat Intelligence Report Date: May 20, 2024 Prepared by: David Brunsdon, Threat Intelligence - Security Engineer, HYAS Cyber Threat Intelligence Analysis This week in the HYAS Insight threat intelligence platform, we found a concerning open directory hosting multiple pieces of malware. Malware Analysis 1.

CyberSecurity Insiders
JANUARY 6, 2022
Many people still don’t realize the dangers of phishing, malware, ransomware, unpatched software, and weak passwords. HTTPS and DNS), data link (e.g., Did you know that human error is the main culprit of 95% of data breaches ? Some of the most important security layers include the network (IP and ICMP), the application (e.g.,

Security Boulevard
JUNE 14, 2023
We founded HYAS with a mission to tackle cyber threats differently — to use our expertise in adversary infrastructure to discover threats before they become attacks. You can deploy HYAS Protect as a cloud-based protective DNS security solution or through API integration with existing cybersecurity services.

CyberSecurity Insiders
JANUARY 25, 2022
. ” The report’s findings are gathered using CSC’s newly launched DomainSec SM platform , which makes the connections between newly registered, dropped, and existing domain names, online brands, and fraud (phishing). At CSC, we believe domain security intelligence is power.

Security Boulevard
MARCH 25, 2025
The domain name system (DNS) is an essential component of the internet, allowing users to access websites using human-readable domain names instead of complex IP addresses. RDAP enables cybersecurity professionals to access structured and authenticated registration data, aiding in threat intelligence and incident response.

Security Boulevard
SEPTEMBER 4, 2024
Urelas malware infiltrates systems through phishing emails containing malicious attachments or links and deploys a range of tactics, including taking screenshots of users’ screens and monitoring their keystrokes. It infiltrates systems through phishing attacks or malicious downloads. Want more threat intel on a weekly basis?

Vipre
JANUARY 25, 2021
Thus, an antivirus is the most important security tool that everyone must have to protect themselves from viruses, malware, trojans, and similar cyber threats. Ad blockers, as the name suggests, block advertisements and protects you from phishing scams. Ad Blockers.

Security Boulevard
SEPTEMBER 18, 2024
Rogue Assets: This malicious infrastructure is created by threat actors to launch cyberattacks against a company. They include malware, phishing sites, and typo squatted domains. Falcon Surface also provides full visibility into internet risks affecting businesses and prioritizes threats based on expert insights and business needs.
eSecurity Planet
FEBRUARY 25, 2022
trading cyber threats – and one disputed NBC News report that outlined possible options presented to U.S. Williams urged viewers to focus on the basics, like phishing , passwords and patching /updating, as those are still the entry point of many attacks. Despite Russia and the U.S. Leverage CTI feeds if you have them.

Security Boulevard
MARCH 13, 2024
While getting into “a land war in Asia” and “going in with a Sicilian when death is on the line” are classic blunders according to cult movie lore, there are classic blunders in cybersecurity we strive to avoid being victimized by - getting phished and falling prey to ransomware or business email compromise are a few that probably top the list.

Approachable Cyber Threats
MARCH 22, 2022
Verizon), DNS resolvers (e.g. These private sector businesses include shopping centers, hospitals, banks, farms, factories, oil and gas, and mass transit, but also big IT services like internet providers (e.g. Cloudflare), authentication platforms (e.g. Okta), and cloud hosting providers (e.g.

Security Affairs
APRIL 6, 2025
CISA adds Apache Tomcat flaw to its Known Exploited Vulnerabilities catalog Apple backported fixes for three actively exploited flaws to older devices Spike in Palo Alto Networks scanner activity suggests imminent cyber threats Microsoft warns of critical flaw in Canon printer drivers CrushFTP CVE-2025-2825 flaw actively exploited in the wild Frances (..)

NetSpi Executives
MARCH 21, 2025
It is essential at the beginning of any cybersecurity strategy, particularly given the increase in cyber threats. This testing helps identify risks like unpatched software, misconfigured DNS, and vulnerable web applications, all possible entry points for external threats.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content