How Modern Security Teams Fight Today’s Cyber Threats
Tech Republic Security
NOVEMBER 9, 2022
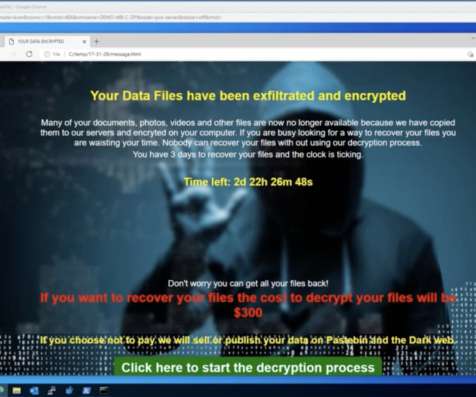
This ebook can help security and IT professionals quickly deploy cloud-based cybersecurity that can easily scale as business needs change and protect users on and off the network. The post How Modern Security Teams Fight Today’s Cyber Threats appeared first on TechRepublic.





























Let's personalize your content