Enhancing Network Security: Best Practices for Effective Protection
Hackology
NOVEMBER 15, 2023
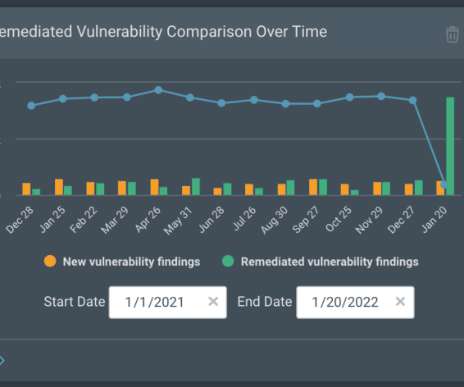
In an era of escalating cyber threats, enhancing network security is paramount. This article explores a comprehensive approach to network protection, encompassing network scanning, vulnerability and patch management, user access controls, network segmentation, and employee training.

















Let's personalize your content