Swiss expert Till Kottmann indicted for conspiracy, wire fraud, and aggravated identity theft
Security Affairs
MARCH 21, 2021
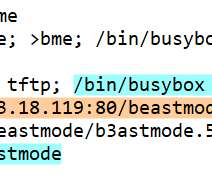
Hackers also posted images captured from the hacked surveillance video on Twitter with an #OperationPanopticon hashtag, published images show that they have gained root shell access to the surveillance cameras used by Telsa and Cloudflare. SecurityAffairs – hacking, cybercrime). ” continues the DoJ.














Let's personalize your content