P-to-P fraud most concerning cyber threat in 2023: CSI
CSO Magazine
JANUARY 24, 2023
CSI), followed by data breaches (23%), ransomware (20%) and a breach at a third party (15%). It was cited by 29% of respondents in a survey by Computer Systems Inc.

CSO Magazine
JANUARY 24, 2023
CSI), followed by data breaches (23%), ransomware (20%) and a breach at a third party (15%). It was cited by 29% of respondents in a survey by Computer Systems Inc.

Security Affairs
DECEMBER 19, 2023
This could encompass customer information, sales records, and financial data. As a result, there’s an elevated risk of sensitive information being stolen and misused for activities such as identity theft, fraud, or sale on the dark web.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 11, 2024
Now Cybersecurity expert says the next generation of identity theft is here: ‘Identity hijacking’ Were 3 Million Toothbrushes Really Used for a DDoS Attack? Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, newsletter)

IT Security Guru
JANUARY 26, 2024
Data Breaches Fleet management systems hold a treasure trove of sensitive data such as driver information, vehicle locations, routes, cargo details and customer data. A data breach could result in the disclosure of this information to hackers who may then commit identity theft, fraud or other illicit activities.
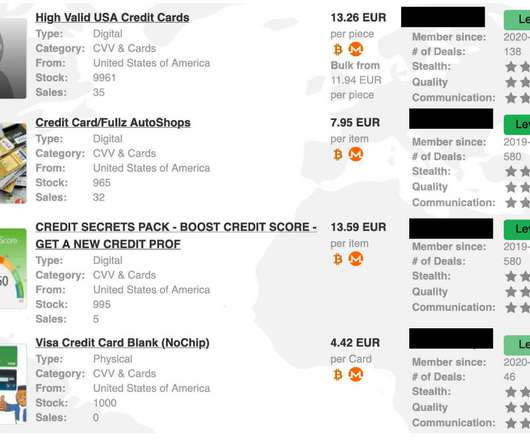
Security Affairs
JUNE 15, 2022
These documents could be used to conduct scams and identity theft. The price varies between $100 up to $120 depending on the volume of data and the source of the data. Dark Web Index 2022 also lists malware infections and DDoS attacks. Price USD (2021) Avg. Additional details are included in the report.

Security Affairs
NOVEMBER 15, 2023
Source: Cybernews The information exposed in this data leak could have been exploited for fraud, identity theft, phishing attempts, or as a source of data for meticulously targeted cyberattacks. Storing personal information in logs should be avoided, as it elevates their sensitivity level. User security log.

SiteLock
AUGUST 27, 2021
Data breaches cost an average of $3.9 With database access, thieves can use the data to commit fraud, blackmail, extortion, identity theft and to turn a quick profit by selling it to other criminals on the dark web. Businesses and consumers in the U.S. lost more than $3.5
Let's personalize your content