News Alert: Traceable AI report exposes true scale of API-related data breaches, top challenges
The Last Watchdog
SEPTEMBER 11, 2023
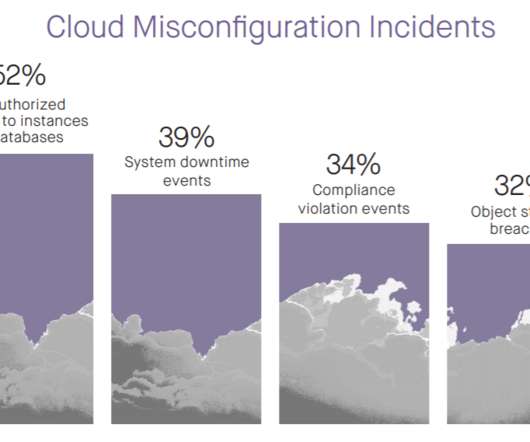
. — Traceable AI, the industry’s leading API security company, today released its comprehensive research report – the 2023 State of API Security: A Global Study on the Reality of API Risk. Traceable believed that it was time to fill this gap and embarked on this research journey with the Ponemon Institute.

















































Let's personalize your content