Critical Actions Post Data Breach
SecureWorld News
DECEMBER 30, 2024
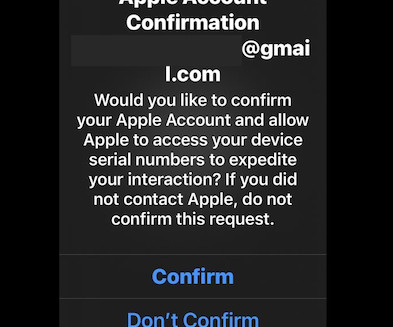
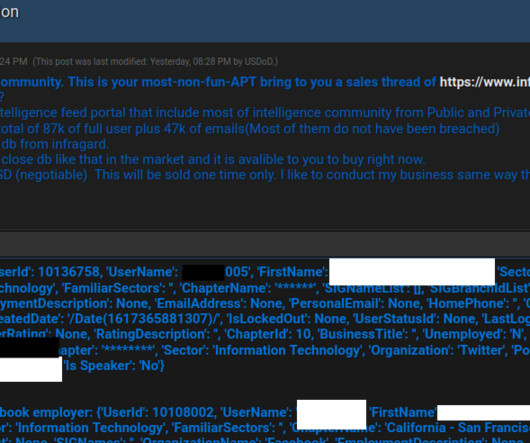
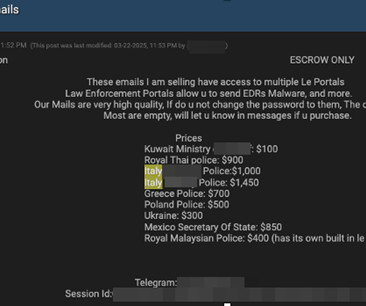
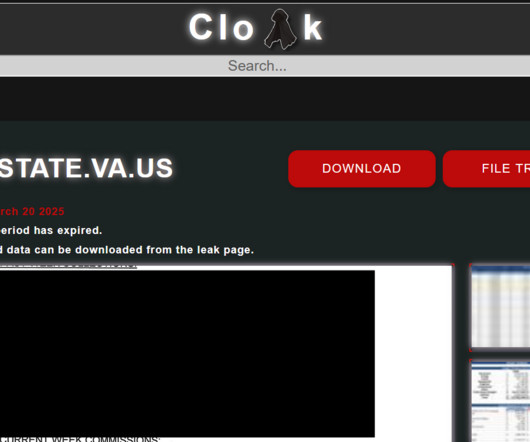
Recent cybersecurity statistics indicate that data breaches are escalating into a significant international concern. This underscores the need not only for strong preventive measures to protect critical information but also for a well-defined strategy to contain the damage if attackers successfully breach your defenses.
















































Let's personalize your content