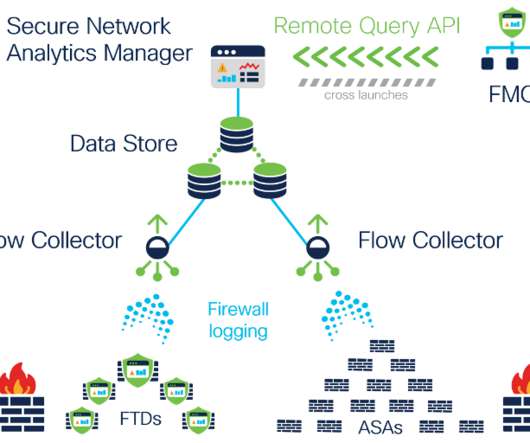
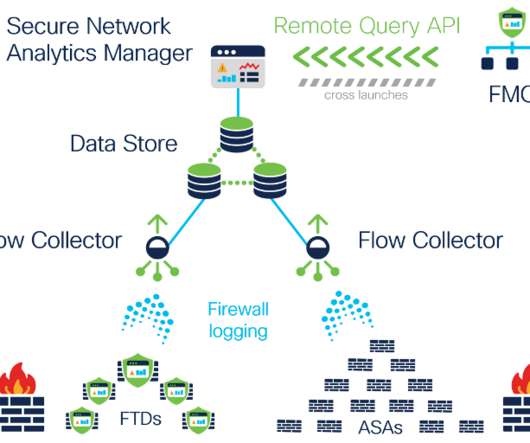
Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
It’s no secret that last year’s abrupt exodus away from corporate offices presented organizations with novel challenges related to monitoring and securing their newly remote workforce. Organizations had always historically experienced visibility gaps into employee activities whenever their users were off-VPN while working remotely.

















Let's personalize your content